Web Application Hacking & Penetration Testing

Why take this course?
🧩 Unlock the World of Web Application Hacking & Penetration Testing
Are you ready to dive into the depths of web application security? With cyber threats evolving daily, understanding and mitigating vulnerabilities has never been more critical. Our course, led by the renowned Vivek Kumar, is your comprehensive guide to mastering Web Application Hacking & Penetration Testing, focusing on the OWASP Top 10 security risks.
Course Overview:
🎓 Who this course is for:
- Security enthusiasts and professionals aiming to enhance their penetration testing skills.
- Developers looking to secure their applications from common vulnerabilities.
- Anyone interested in understanding the intricacies of web application security.
Key Features:
-
Practical Approach: Learn by doing with hands-on tutorials on setting up your own Xampp server and installing vulnerable applications. Gain real-world experience and confidence as you apply what you learn.
-
Cloud Relevance: Whether your applications reside in the cloud, on physical servers, or within VMs, this course equips you with the skills to identify and exploit vulnerabilities in any environment.
Course Highlights:
- 🛡️ OWASP Top 10 Coverage: Dive deep into the top security risks for web applications:
- Injection - Master SQL and Command Injection techniques.
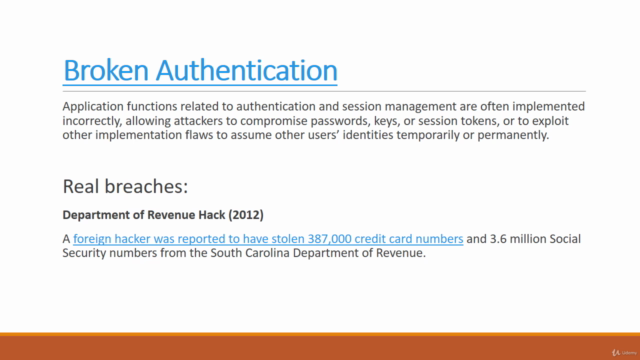
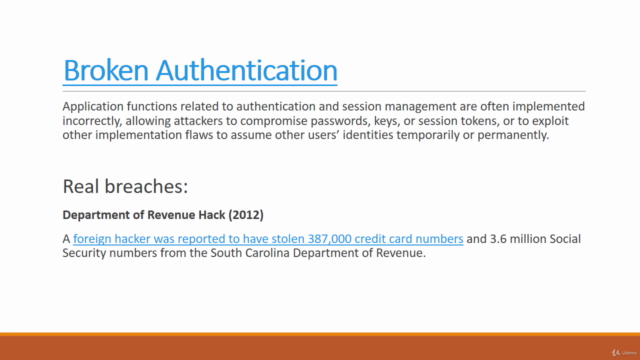
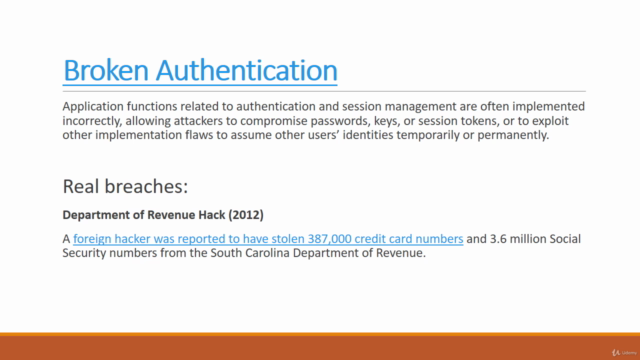
- Broken Authentication - Learn to test authentication mechanisms.
- Sensitive Data Exposure - Understand how to protect sensitive data.
- XML External Entities (XXE) - Explore methods to exploit and prevent XXE attacks.
- Broken Access Control - Test and improve access control measures.
- Security Misconfiguration - Identify misconfigurations that could compromise security.
- Cross-Site Scripting (XSS) - Learn the various XSS attack vectors and how to defend against them.
- Insecure Deserialization - Understand deserialization vulnerabilities and their exploitation.
- Using Components with Known Vulnerabilities - Recognize components that pose risks and learn to replace them with secure alternatives.
- Insufficient Logging & Monitoring - Implement comprehensive logging and monitoring strategies to detect attacks effectively.
Why Choose This Course?
-
🖥️ Cutting-Edge Content: Our curriculum is up-to-date, covering the latest in web application security, including cloud-based vulnerabilities.
-
🌍 Global Skillset: This course is not limited to physical servers; it prepares you for real-world cloud deployments.
Learning Outcomes:
By the end of this course, you will:
- Have a clear understanding of the OWASP Top 10 security vulnerabilities in web applications.
- Be equipped with practical skills to identify and exploit these vulnerabilities responsibly.
- Have installed and understood the use of vulnerable applications on your local environment.
- Be prepared to protect your own web applications against a wide range of attacks.
Ethical Consideration:
This course is for educational purposes only. Ethical hacking is about understanding vulnerabilities to better defend against them. We encourage all participants to use the knowledge gained responsibly and within the bounds of the law.
🎓 Embark on your journey to becoming a security expert today! With Vivek Kumar's guidance, you'll be equipped with the skills needed to keep web applications secure from the ever-evolving threats in the cyber world.
Enroll now and transform your cybersecurity career with our Web Application Hacking & Penetration Testing course!
Course Gallery
Loading charts...