Top 5 Tools & Tricks for Ethical Hacking & Bug Bounties 2025

Why take this course?
🚀 Course Title: Top 5 Tools & Tricks for Ethical Hacking & Bug Bounties 🛡️ [2021 Edition]
🔥 Course Headline: Master the Most Commonly Used Industry Tools for Ethical Hacking, Penetration Testing & Bug Bounty Hunting!
Course Description:
Welcome to "Top 5 Tools & Techniques for Pentesting in Cyber Security Course"! 🎓
This comprehensive course is designed for beginners as well as intermediate cyber security enthusiasts who aspire to master the art of ethical hacking, penetration testing, and bug bounty hunting. With no prior hacking knowledge required, you'll embark on a journey to understand, apply, and master the top 5 tools used by professionals in the industry.
Why Choose This Course?
- Practical Learning: Engage with hands-on experience using real-world tools.
- Industry Relevant Tools: Learn about the tools that are currently in demand within the cyber security sector.
- Step-by-Step Guidance: From basics to advanced techniques, this course covers it all.
- Ethical Approach: All practices are taught ethically and responsibly, ensuring you can perform vulnerability hunting without breaking the law.
What You'll Learn:
Nmap: 🌐
- Understanding Nmap and its importance.
- Step-by-step installation guide.
- Master firewall bypass techniques.
- Use a comprehensive Nmap cheatsheet to streamline your scanning processes.
Burp Suite: 🛡️
- Learn what Burp Suite is and how it fits into the penetration tester's toolkit.
- Get hands-on with installation and see practical examples of interception.
- Solve a real-time Capture The Flag (CTF) challenge using Burp Suite.
Content Discovery: 🔍
- Understand Project Discovery's dataset to enhance your bug bounty hunting skills.
- Identify subdomains and leverage them for more effective vulnerability hunting.
Google Hacking Database (GHDB): 🔎
- Dive into the world of Google dorks and learn how to hunt for sensitive files.
- Create your own custom Google dork queries.
IOT Search Engines (Shodan/Censys/Grey Noise): 🌟
- Explore the Internet of Things (IoT) search engines for exposed devices and services.
- Perform banner grabbing to identify vulnerable systems.
- Utilize shodan search filters to refine your active enumeration.
GitHub Reconnaissance: 🛠️
- Uncover sensitive data from GitHub repositories that could be reported as critical vulnerabilities (P1 severity).
- Learn both automated and manual methods of GitHub reconnaissance.
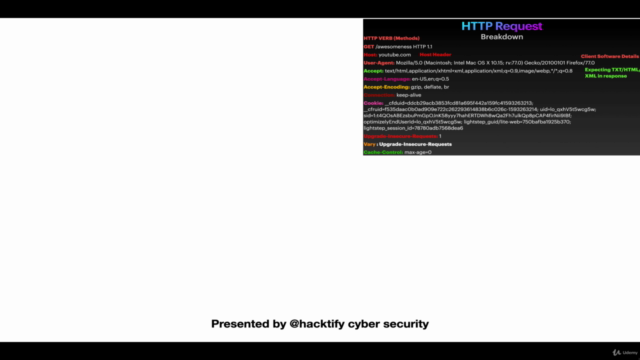
Anatomy of an HTTP Request: 💻
- Understand the components of an HTTP request and their headers.
- Learn how different headers can affect your security posture.
Course Benefits:
- 24/7 Support: Have questions? Post them in our Q&A section and receive prompt assistance!
Important Notes:
- Educational Purpose Only: This course is intended for educational purposes to learn about ethical hacking. All vulnerabilities found during the course are responsibly reported and fixed.
- Responsible Use of Tools: Always remember that testing any website without a Responsible Disclosure Policy in place is unethical and illegal. The author bears no responsibility for such actions.
Join us on this thrilling journey into the world of ethical hacking and bug bounties! Let's make cyberspace a safer place together. 🛡️➡️🚀
Don't miss out on these top tools & tricks for ethical hacking, penetration testing, and bug bounty hunting. Enroll in the course today and start your transformation into a cyber security professional! 🎓✨
Course Gallery


Loading charts...