OWASP Top 10: Comprehensive Web Application Security

Why take this course?
🛡️ Master OWASP Vulnerabilities and Hacking Techniques: OWASP Top 10 🛡️
Course Headline: Master OWASP Top 10 Attacks
Embark on a journey to master web application security by understanding the OWASP Top 10 vulnerabilities and the hacking techniques associated with them. This comprehensive course, "Ultimate Guide to Web Application Security OWASP Top Attacks," is designed to equip you with the knowledge to not only recognize these common attacks but also to exploit them so you can fortify your systems against such threats.
Course Description:
Section 1: Introduction to OWASP Top 10 Attacks
- OWASP Top Attacks Unveiled: Gain insight into the most prevalent security risks targeting web applications, as identified by the Open Web Application Security Project (OWASP).
- Exploitation Techniques: Learn how these vulnerabilities are exploited in real-world scenarios, providing a deep understanding of attacker methodologies.
Section 2: Hands-on with DVWA and OWASP BWA
- Live Demonstrations: Engage with the Damn Vulnerable Web Application (DVWA) and OWASP Broken Web Applications (BWA) to see these vulnerabilities in action.
- Practical Exercises: Perform extensive exercises that will give you a clear understanding of how attacks are executed and what happens behind the scenes.
Section 3: Reconnaissance and Tooling
- Domain Information Gathering: Learn effective techniques to gather information about a target domain and identify potential vulnerabilities.
- Hacker's Toolkit: Explore the tools most commonly used by hackers, including an in-depth look at the Kali Linux distribution.
Section 4: Advanced Penetration Techniques
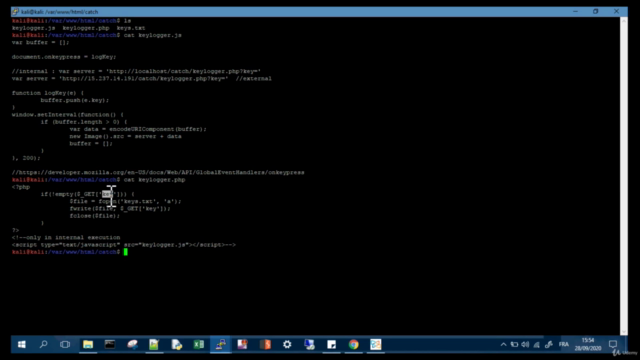
- Scripting for Penetration Testing: Code your own scripts to get hands-on experience with advanced penetration testing, learning to forge tools when necessary.
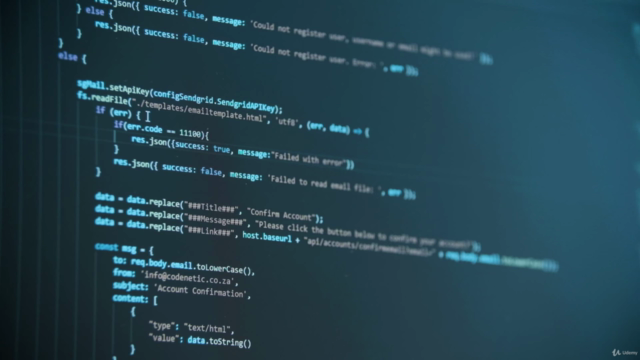
- Attacks Covered: Dive into various attacks such as SQL Injection, Command Injection, Cross-site Scripting (XSS), Cross-site Request Forgery (CSRF), Path Traversal, and File Inclusion, among others.
Course Features:
✅ Comprehensive Coverage: Learn about the OWASP Top 10 vulnerabilities in detail. ✅ Live Hacking Exercises: Practice your skills with real-world tools and applications. ✅ Educational Tools: Understand the tools attackers use, including Kali Linux. ✅ Scripting Basics: Write your own penetration scripts to gain a deeper understanding of system vulnerabilities.
Important Note:
🚫 Legal Disclaimer: This course is intended for educational purposes only. It is crucial to have explicit authorization before using these techniques on systems or assets you do not own. Misuse of the knowledge and methods presented in this course is strictly prohibited and can lead to legal consequences. The instructor holds no responsibility for any illegal actions taken based on this course content.
Join the Community:
If you find this course informative and helpful, please consider giving it a rating and sharing it with your peers and colleagues. Your feedback is invaluable for continuous improvement and ensuring that this knowledge reaches as many professionals as possible who are dedicated to securing our digital world against cyber threats.
Course Gallery


Loading charts...