Learn Ethical Hacking / Pen testing & Bug Bounty Hunting A:Z

Why take this course?
🚀 Welcome to "Learn Ethical Hacking / Pen testing & Bug Bounty Hunting A:Z"! 🛡️
This comprehensive Ethical Hacking tutorial is meticulously designed for both beginners and seasoned professionals looking to master the art of ethical hacking, penetration testing, and bug bounty hunting. 💻✨
Course Overview:
Our journey into the world of cybersecurity will cover the installation of essential software, followed by an in-depth exploration of the four core aspects of penetration testing:
-
Network Penetration Testing 🌐
- Understand how networks operate and secure data transmission.
- Crack Wi-Fi keys to gain access to wireless networks.
- Learn the principles of network security and how to protect sensitive information.
-
Gaining Access 🚪
- Connect to unencrypted networks and sniff out valuable data.
- Adapt to various network setups, including wired and wireless connections.
- Overcome encryption barriers like WEP, WPA, and WPA2 to access targeted systems.
-
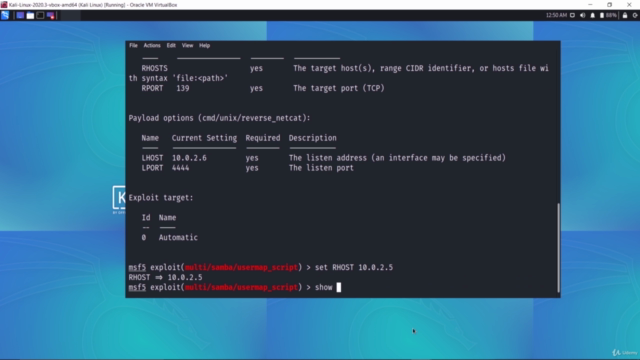
Post-Connection Attacks 🔍
- Perform attacks on networks after successful connection establishment.
- Explore post-exploitation tactics, including file system interaction, executing system commands, and accessing webcams.
-
Website / Web Application Hacking 🌐
- Gain insights into the inner workings of websites and applications.
- Discover and exploit vulnerabilities to compromise website security.
- Learn how to protect your own systems against similar attacks.
Course Structure:
-
Network Penetration Testing 🛫
- Get a grasp of network fundamentals and cybersecurity concepts.
- Master the art of cracking passwords and gaining unauthorized access to networks.
-
Gaining Access 🔑
- Learn how to ethically breach systems using various methods and tools.
- Understand encryption and how to work around it without crossing ethical lines.
-
Post-Connection Attacks 🚫
- Discover the dark art of post-exploitation, learning how to navigate a system once access has been gained.
- Perform actions such as executing scripts or manipulating data with full system privileges.
-
Website / Web Application Hacking 🛠️
- Delve into the realm of web hacking and uncover the secrets to vulnerability discovery.
- Learn techniques to exploit weaknesses and understand how to strengthen your website defenses.
Who Should Take This Course? 👥
- Aspiring Ethical Hackers 🕵️♂️
- Curious Individuals 🤓
- Cybersecurity Enthusiasts 🛡️
- Professionals Seeking to Enhance their Skills 🏫
Important Notes:
- This course is strictly for educational purposes. 📚
- All demonstrations are conducted in a controlled environment or with explicit permission. 🕵️♂️✨
By the end of this A:Z Ethical Hacking tutorial, you'll have the knowledge and skills to think like a black hat hacker while staying on the right side of the law. 🛡️💫
Join us on this exciting journey into the world of cybersecurity and become a pro at ethical hacking, penetration testing, and bug bounty hunting! 🚀🌐🔐
Course Gallery

Loading charts...