Surviving Digital Forensics: Resolving Attached USBs

Why take this course?
🚀 Surviving Digital Forensics: Resolving Attached USB 🔎 GroupLayout your digital detective skills with our comprehensive course led by seasoned expert, Michael Leclair! 🕵️♂️
Course Overview:
This isn't just any forensic guide; it's a deep dive into the intricate world of linking USB activity to Windows computer systems. Whether you're an IT professional, cybersecurity enthusiast, or a legal expert in need of tangible digital evidence, this course equips you with the knowledge and techniques to trace USB device usage effectively.
What You'll Learn:
- 🛡️ The Essentials of Digital Forensics: Understand the fundamentals of digital forensics and its significance in a cybersecurity context.
- 🧙♂️ USB Activity Tracking: Master the tools and methods to track and analyze USB activity on Windows systems.
- 🔍 Evidence Collection Techniques: Learn how to collect voluminous amounts of data with precision and accuracy.
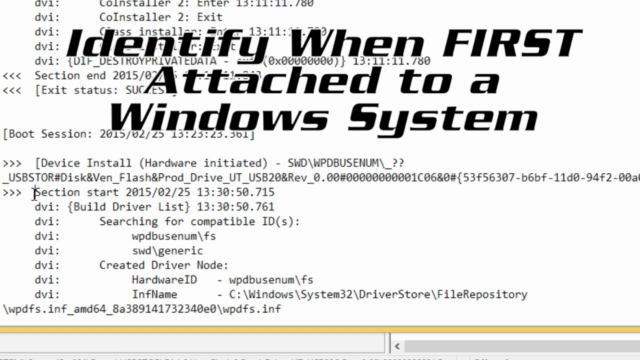
- ⏱ Time-based Analysis: Gain insights into when USB devices were attached to a system, crucial for timeline analysis.
- 🚫 Unauthorized Access Detection: Determine if unauthorized or suspicious USB devices were used.
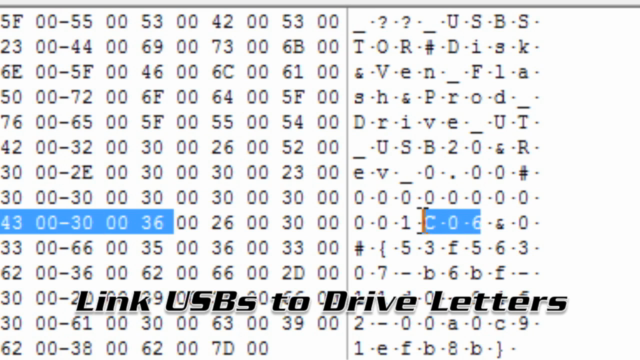
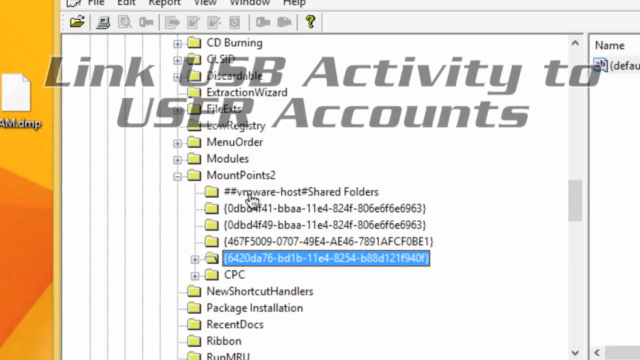
- 🤝 User Account Association: Identify which user accounts were responsible for mounting and using the USB volumes.
Course Highlights:
- Hands-on Learning: Engage with real-world scenarios and step-by-step guidance through practical exercises.
- Freely Available Tools: Utilize open-source tools to ensure you're working with industry-standard software.
- Approximate Course Duration: Expect to complete the course within an hour, with the potential for more in-depth exploration of topics as desired.
- Real-World Applications: Apply what you learn directly to your work or research, enhancing your investigative capabilities.
Why This Course?
- Expert Instruction: Learn from an instructor with extensive experience in the field, Michael Leclair.
- Practical Skills: Transition theory into practice with hands-on exercises and real-life examples.
- Easy to Follow: Designed for clarity and ease of understanding, even for beginners in digital forensics.
- Certification Ready: Prepare yourself to handle complex scenarios that could lead to a certification in digital forensics.
Who Should Take This Course?
- IT Professionals seeking to bolster their incident response and forensic analysis skills.
- Cybersecurity Analysts looking for advanced techniques to enhance their digital investigations.
- Legal and Law Enforcement Officers who require forensic evidence collection and presentation in a legal context.
- Forensic Specialists aiming to expand their expertise to include USB device tracking on Windows systems.
Join us in this enlightening journey through the complexities of digital forensics, where every byte counts and your ability to trace the digital footprints can make all the difference. 💻✨
Enroll now and take your first step towards mastering USB activity tracking within Windows computer systems! 🚀🔗
Course Gallery

Loading charts...