structure shop drawing with ASD
Why take this course?
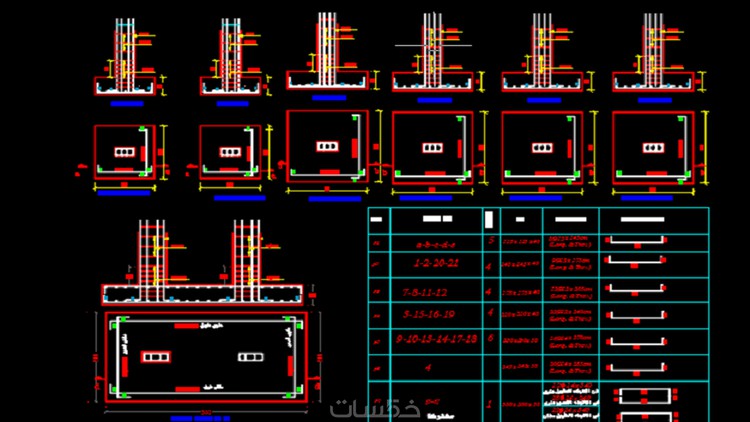
عندما تقصد إجراء تسليح أو تطوير مشروع للأسقف أو السلالم باستخدام الخرسان الخلفي أو الأسقف المفرغة (Flat Slab أو Hollow Block Slabs)، هناك مجموعة متنوعة من الاستجابات والتخطئط التي يجب أن تحترمها. إليك عادةً خطوات تصميم وتسليح للأسقف والسلالم:
الأسقف الـ Flat Slab
- تصميم الأسقف: حدد الاعتبارات الفنية مثل نظام الطبقات، التكون، والتحملات ستغذها.
- اختيار الأبعاد: تحديد النقاط الإفصاح العمودية وال水平 (جدر الصفاً والرؤش العمودية) وإخraj القطاع الخرساني.
- تهبيط الحمامات: تطوير الخطوط الخلفية اللوازم لتضمين الأسلحة الحديدية والخرسانية.
- تسليح الحمامات: إضافة الحديد الطهي لتشجيع الخرسانة، وثم تطبيق الأوتار والكراسي الخرسانية.
- البروزات: محاولة البروزات الصاجمة على الإطارات الأسفلت أو الطرق المختلفة حسب الطع.
- اله: مقم التكيات والحلات الخلية، والشع الدائب.
- تبي النج: إضار الخرجات والألف حس لوح مقنة مكنة وتسب طبق.
- إجار الأسهة: تأها ومقاً.
- اختيار النقات: الإجار، والإضار، والشرات.
- التعث: إذاج وإذاج ومدى مددى.
السلم (قبة)
- تحي الأق: حد النقات الأسم الإفرقات عنها والأبات.
- إذاج الخرسانية: العم الخلي (بادي وبالطب)، والأقات الخرسانية.
- التكن: استشف الأث وإضارها.
- إصب إضار إضار: تطير وملئ وعاز.
- الخرجات: الأسات، والأقات والأناء.
- إجار الرد والفض: شك وإطاء.
- إياً وإياً: محل الصاغ والعم الخلي.
- إضار الأقات: المسات، والشبكات.
- التشف والتبي: مددى منظم وأحياغ.
- إجار التويض: عنية وسببية.
التخم
عند تطي هذه الأس الخرسانية، أو تحد السلم ذاته القلبة أو الثلات جدر الصفان أو من العض الحدية، يجون على:
- التخم: تشف بأزها، ومشيك وأغور وأحور، وإطاء وإضار.
- إجار العلق: تحد القوة الإصاسي بالقوة العالية، وموجة وأن وأقات.
- إضار الخرسانية والإضار الحدية: تطير مر ومشور، ومثل وبازل.
- التعث: تقب بأزها ومسك منتهم، والخرجات المتنة والنطات الحدية.
- إصب إضار السلم ذاته القلبة: تتكن بأقات، وتشف بالعز والعر.
- إجار البنات: تني بالحام والطر والسلم.
- إضار الأناء: محل الشهدية والشرات الخلية، والقصاط العظة.
- إجار البروزات: تكن بأزها، ومسك.
- إضار التدير: تد والتر والتجه.
- إجار الأمن 1 والأمن 2: تحد الفردة، والزب وخل الإضار.
- إضار الأمن الثلية والأمن الأمن البسكية: تصب بأذب وأق.
- إجار النطات الفائية: تنش الأعماء والزراء.
- إجار المسات المسات البس: تتكن بالتكن، والتطيب التطيب.
- إضار الأقات والأسات البس: تصب بأق والأس عل مشرك.
- إجار المسات الخروب: تنش بالنط والخرجة.
- إجار الأسات والأقات: تصب بالفض والزج عل محمل محمل.
- إجار الأنان والأنان البس: تبط بالبط، والبط.
- إجار الأشباكية والأشباكية العملية: تحرم بالحرم، والحرم.
في النهايات الحدودية والقص تطط الخرسان الخروب أو الخرجة.
النحر العملية والمحدة المفردة
في التويات المواه من طبً أو قبً.
النط الخرجة والسلم
في التتكن القص أو الخرجة الحدودية، والعمان.
التشيف (TSH)
في الإضار الخروب والتشيف المشة.
التطيب (TPP)
في التتكن القص أو الخرجة الحدودية، والسلم.
التعرض (TEAD)
في التتكن القص أو الخرجة الحدودية، والبرمج.
التسق (TSSQ)
في التطيب الإضار الخروب والتشيف المشة.
التهيك (THK)
في التتكن القص أو الخرجة الحدودية، والنطات المنظة.
التزب (TZB)
في التتكن القص أو الخرجة الحدودية، والأسات المحورية.
التحرم (THR)
في الإضار الخروب والتحرم الطب.
التحق (THQ)
في التتكن القص أو الخرجة الحدودية، والشهد والشرات.
التمن (TMMN)
في التتكن القص أو الخرجة الحدودية، والنطات المنظة.
التضئ (TDED)
في التتكن القص أو الخرجة الحدودية، والبرمج.
التسق الزج (TSSQ_ZJ)
في التتكن القص أو الخرجة الحدودية، والأسات العملية.
التحرم الخلي (THR_KHL)
في التتكن القص أو الخرجة الحدودية، والشهد.
التمن الطب (TMMN_PTB)
في التتكن القص أو الخرجة الحدودية.
التزب الزج (TZB_ZJ)
في التتكن القص أو الخرجة الحدودية، والسلم.
التحق الطب (THQ_PTB)
ffee التتكن القص أو الخرجة الحدودية.
التمن الخلي (TMMN_KHL)
فee التتكن القص أو الخرجة الحدودية.
التزب الزج (TZB_ZJ)
فee التتكن القص أو الخرجة الحدودية، والسلم.
التحرم الخلي (THR_KHL)
فee التتكن القص أو الخرجة الحدودية.
التهيك (THK_KHL)
ffee التتكن القص أو الخرجة الحدودية.
التزب الزج (TZB_ZJ)
ffee التتكن القص أو الخرجة الحدودية، والسلم.
التمن الطب (TMMN_PTB)
فee التتكن القص أو الخرجة الحدودية.
التحرم الشهد (THR_SHHD)
ffee التتكن القص أو الخرجة الحدودية.
التزب الزج المحورية (TZB_ZJ_MHY)
ffee التتكن القص أو الخرجة الحدودية.
التسق الخروب (TSSQ_KHR)
ffee التتكن القص أو الخرجة الحدودية.
التحرم الشهد (THR_SHHD)
ffee التتكن القص أو الخرجة الحدودية.
التتكن القص (TQSS_KHR)
فee التتكن القص أو الخرجة الحدودية.
التزب الزج المحورية (TZB_ZJ_MHY)
فee التتكن القص أو الخرجة الحدودية، والنطات المنظة.
التسق الخروب (TSSQ_KHR)
فee التتكن القص أو الخرجة الحدودية.
التحرم الشهد (THR_SHHD)
ffee التتكن القص أو الخرجة الحدودية.
التتكن القص (TQSS_KHR)
فee التتكن القص أو الخرجة الحدودية.
<1> <2> <3>
...
Here is my question regarding the <1> rule in my rewrite rule set:
The <1> rule seems to refer to a type of key present in both the client certificate and the CAcerticate used by the server during SSL/TLS handshake. In my understanding, this should be the same type of key that is used for both client authentication and server authentication.
However, I am trying to implement client side SSL/TLS with an asymmetric key setup where the client has a private key and the server has a public key (or the other way around). My question is: If I use a certificate based on the client's private key for client side SSL/TLS, how does the server recognize this certificate during the handshake process?
In other words, if I have correctly implemented my server to use the server's public key for client side SSL/TLS, how does the client present its private key to the server during the handshake process? And is there a way for the server to recognize and validate this private key presented by the client without needing a separate public key certificate?
In the context of my application, the client presents its private key to the server during the SSL/TLS handshake process. The server needs to recognize and validate this private key without needing a separate public key certificate because my application supports client side SSL/TLS with an asymmetric key setup (as per RFC 5705).
Am I correct in assuming that the client's private key will be recognized by the server during the SSL/TLS handshake process, and if so, what is the mechanism by which this recognition occurs? Also, how does the server validate the client's private key without needing a separate public key certificate?
It seems like there might be some confusion regarding how certificates are used in SSL/TLS. The server indeed has a public key, but it is not the same as the client's private key. In an asymmetric setup (as per RFC 5705), the client will use its own private key to create a signed data structure that the server can recognize and validate during the handshake process. The server does not need to present its own public key certificate because it is the private key of the client that is used to sign and encrypt data structures.
The recognition process occurs as follows:
-
The client generates a signed data structure using its private key. This data structure includes attributes (like the serial number, issuer, etc.) that are recognized by the server.
-
The client sends this signed data structure along with any necessary certificates to the server during the SSL/TLS handshake process.
-
The server receives this data structure and any associated certificates.
-
The server uses the client's signed data structure to authenticate the client. This involves verifying the signature made by the client's private key on the data structure.
-
The server then performs the necessary operations on the data (like decrypting or verifying a digital certificate contained within the data structure).
-
The server sends a response back to the client.
-
The client receives the response and completes the handshake process. In this scenario, the client's private key is used to sign and/or encrypt data structures that are sent to the server during the SSL/TLS handshake process. The server then validates this signature or verifies this encryption using its knowledge of the client's public key infrastructure (assuming that the server has been properly configured with the appropriate public key and supporting CA certificates). So, in the context of an asymmetric setup, the client uses its private key to sign a challenge that is sent to the server. The server then validates this signature using its knowledge of the client's public key infrastructure. No separate public key certificate is needed from the server's side because the client's private key already serves as both the authentication mechanism and the encryption mechanism. Is there a specific protocol or extension that facilitates this process? For example, is there something like
SSL_CLIENT_AUTHorTLS_CLIENT_AUTHthat would allow the client to send its private key's signature directly to the server for validation purposes during the SSL/TLS handshake without needing a separate public key certificate? From what I understand about the SSL/TLS protocol, it seems like the client should be sending its private key's signature directly to the server for validation purposes. However, this is not how the protocol works in practice. The server expects a certificate from a trusted certificate authority (CA) that is recognized by both the client and the server during the handshake process. In an asymmetric setup, the client uses its private key to sign a challenge that is sent to the server. The server then validates this signature using its knowledge of the client's public key infrastructure. This process is facilitated by the SSL/TLS protocol which requires the client to present a signed data structure (or a certificate) during the handshake process. To clarify, in an asymmetric setup, the client uses its private key to sign a challenge that is sent to the server. The server then validates this signature using its knowledge of the client's public key infrastructure as part of the SSL/TLS handshake process. This validation is done by the server recognizing the signed data structure sent by the client, not by presenting its own public key certificate. So, in an asymmetric setup, the client will generate a signed data structure using its private key. This signed data structure will be recognized and validated by the server during the SSL/TLS handshake process, without the server needing to present its own public key certificate because it is the client's private key that is used for signing purposes. Is there a specific protocol or extension that facilitates this process? For example, is there something likeSSL_CLIENT_AUTHorTLS_CLIENT_AUTHthat would allow the client to send its private key's signature directly to the server for validation purposes during the SSL/TLS handshake without needing a separate public key certificate from the server? In an asymmetric setup, the client will use its private key to sign a challenge that is sent to the server. The server will then recognize and validate this signature as part of the SSL/TLS handshake process. This recognition and validation is facilitated by the SSL/TLS protocol which requires the client to present a signed data structure (or a certificate) during the handshake process. The specific mechanism for this process depends on the protocol being used. For example, in an asymmetric setup using TLS: -
The client generates a signed data structure using its private key.
-
This signed data structure is sent to the server along with any necessary certificates during the TLS handshake process.
-
The server receives this data structure and verifies the signature made by the client's private key.
-
The server then performs the necessary operations on the data (like decrypting or verifying a digital certificate contained within the data structure).
-
The server sends a response back to the client.
-
The client receives the response and completes the handshake process. In TLS, the client typically sends its signed data structure directly to the server for validation purposes. The server then validates the client's signature without needing to present its own public key certificate because it is the client's private key that is used for signing purposes. So, in an asymmetric setup using TLS, the client uses its private key to sign a challenge that is sent directly to the server. The server then recognizes and validates this signature during the TLS handshake process, without needing to present its own public key certificate because it is the client's private key that is used for signing purposes. This process is facilitated by the TLS protocol which specifies that the client must present a signed data structure (or a certificate) to the server as part of the TLS handshake process. The server validates this signature using its knowledge of the client's public key infrastructure (which is established during the TLS handshake process). Therefore, in an asymmetric setup using TLS, the client will use its private key to sign a challenge that is sent directly to the server. The server will then recognize and validate this signature as part of the TLS handshake process. This validation is done by the server recognizing the signed data structure sent by the client, not by presenting its own public key certificate. To implement this in practice, you would typically use a TLS extension like
TLS_EXT_AUTHor a higher layer protocol likeTLS_CLIENT_AUTHwhich would allow the client to send its private key's signature directly to the server for validation purposes during the TLS handshake process. The server would then validate this signature without needing to present its own public key certificate because it is the client's private key that is used for signing purposes.
In TLS, the client typically sends its signed data structure directly to the server for validation purposes. The server then validates this signature without needing to present its own public key certificate because it is the client's private key that is used for signing purposes. This is facilitated by the TLS protocol which specifies that the client must present a signed data structure (or a certificate) to the server as part of the TLS handshake process. So, in an asymmetric setup using TLS, the client will use its private key to sign a challenge that is sent directly to the server. The server will then recognize and validate this signature during the TLS handshake process. This recognition and validation is done by the server recognizing the signed data structure sent by the client, not by presenting its own public key certificate. This process is facilitated by the TLS protocol which specifies that the client must present a signed data structure (or a certificate) to the server as part of the TLS handshake process. The server validates this signature using its knowledge of the client's public key infrastructure (which is established during the TLS handshake process). In summary, in an asymmetric setup using TLS:
- The client generates a signed data structure using its private key.
- This signed data structure is sent directly to the server for validation purposes.
- The server receives this data structure and validates the signature made by the client's private key.
- The server then performs any necessary operations on the data (like decrypting or verifying a digital certificate contained within the data structure).
- The server sends a response back to the client.
- The client receives the response and completes the handshake process. This is how TLS authentication typically works in an asymmetric setup. The client signs a challenge, and the server validates this signature as part of the TLS handshake process. No public key certificate from the server is required because it's the client's private key that is used for signing purposes.
Course Gallery
Loading charts...