NEW: Spring Boot 3 Securing Your Application with JWT Token

Why take this course?
🎉 Spring Security with JWT: Protect Your Applications from Unauthorized Access [NEW] [2023] 🔒
Course Overview 🚀
Are you ready to fortify your Spring Boot applications against unauthorized access and secure your data effectively? Our comprehensive course, "Spring Security with JWT: Protect Your Applications from Unauthorized Access," is the ultimate guide to implementing robust security measures in your applications using Spring Security and JSON Web Tokens (JWT).
What You'll Learn 📚
-
Spring Security Essentials: Dive into the fundamentals of Spring Security, a powerful module designed to handle authentication and authorization within Spring-based applications.
-
Implementing JWT Authentication: Learn how to leverage JWT for authentication purposes, ensuring secure token exchange between clients and servers.
-
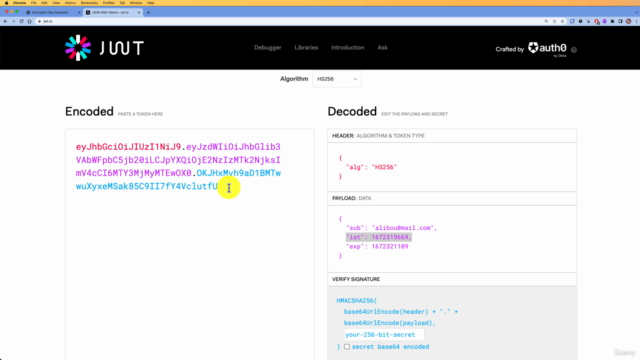
JWT Token Structure: Uncover the intricacies of JWT tokens, which consist of a header, payload, and signature, all encoded in a compact and URL-safe manner.
-
Registration and Public Claims: Get to know the standard claims defined in the IANA JSON Web Token Registry, including
iss(issuer),sub(subject),aud(audience), andexp(expiration time). -
Custom Private Claims: Understand how to create and use private claims tailored to your specific security needs.
-
Secure Signing Algorithms: Explore various signing algorithms such as HMAC SHA256 or RSA, and learn how to sign your JWT for verification purposes.
Course Format 🖥️
Our course is designed with your learning experience in mind:
-
Interactive Lectures: Engage with bite-sized, easy-to-understand content that covers all the essentials of Spring Security and JWT.
-
Hands-On Exercises: Apply what you learn through practical exercises that reinforce key concepts and skills.
-
Lifetime Access: Revisit the course materials anytime to sharpen your knowledge or catch up on any missed content.
Why Secure Your Application with JWT? 🤔
-
Stateless Authentication: JWT enables stateless authentication, allowing for a scalable and flexible security solution.
-
Security: Leverage JWT's cryptographic signature to protect your application against unauthorized access and ensure data integrity.
-
Ease of Use: Simplify the authentication process with tokens that can be easily passed in HTTP headers or POST parameters.
Course Outline 🗺️
-
Introduction to Spring Security
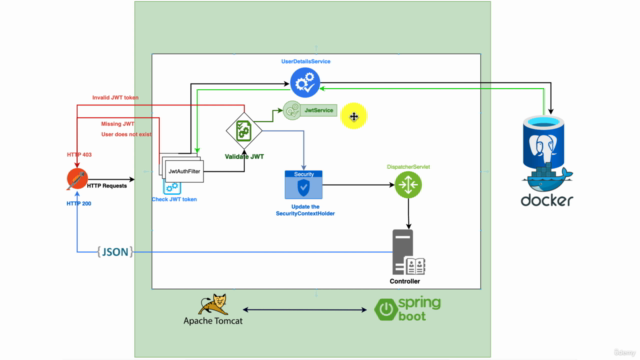
- Understanding the role of Spring Security in application security
- Exploring the architecture and core features of Spring Security
-
Understanding JWT
- The three components of a JWT: header, payload, and signature
- How JWT provides a stateless way to represent claims
-
Registered Claims
- Detailed explanation of
iss(issuer),sub(subject),aud(audience), andexp(expiration time) - Recognizing the value of standard claims for interoperability
- Detailed explanation of
-
Creating Public Claims
- How to define custom public claims as per your security requirements
-
Implementing Private Claims
- Utilizing private claims for sharing secret information between parties
-
JWT Signature and Verification
- Understanding the importance of a secure signature
- Implementing signing algorithms like HMAC SHA256 or RSA
-
Best Practices for JWT Security
- Ensuring the safe handling and transmission of tokens
- Strategies for mitigating common security threats
Enroll now in "Spring Security with JWT: Protect Your Applications from Unauthorized Access" to stay ahead in securing your Spring Boot applications. Secure your applications, secure your data, and take control of your application's integrity with the power of Spring Security and JWT! 🛡️
Don't let security vulnerabilities put your applications at risk. With this course, you'll be equipped with the knowledge to implement secure authentication and authorization mechanisms, ensuring that only authorized users can access your application's resources. Join us and elevate your application security game today! 🌟
Course Gallery
Loading charts...