Red Team: Weaponizing Windows Shortcut (lnk) file Hands-on

Why take this course?
Course Title: Red Team: Weaponizing Windows Shortcut (LNK) File Hands-On 🚀
Course Headline: Master the Art of Compromise with LNK Files in a Windows Environment! 🛠️💻
Course Description:
Windows shortcut (LNK) files are ubiquitous and seemingly benign, but they can be a powerful tool for cyber attackers. In this comprehensive course, P Ahmad will guide you through the modern techniques of weaponizing LNK files to exploit Windows systems. Whether you're a Red Team member, penetration tester, or an ethical hacker looking to expand your skill set, this course will equip you with the knowledge and hands-on experience necessary to effectively leverage LNK files in your cyber operations. 🛡️
Why This Course?
-
Real-World Applications: Learn techniques that are not only theoretical but have been successfully employed in real-world scenarios by top Red Teams and penetration testers.
-
Hands-On Practice: Engage with interactive labs that allow you to apply what you learn in a safe, controlled environment.
-
Stay Ahead of the Curve: Gain an edge over your peers by mastering cutting-edge tactics that abuse LNK files to gain initial footholds and establish persistence in target environments.
What You'll Learn:
-
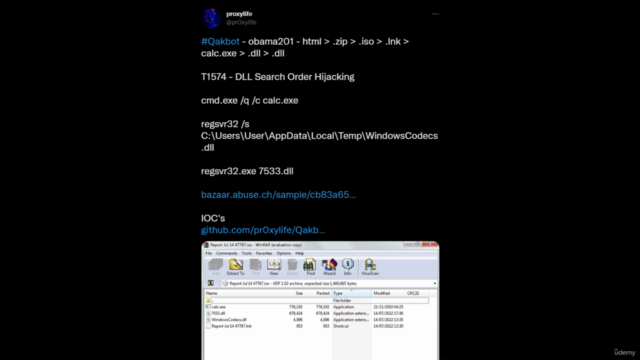
Understanding LNK Files: Dive into the inner workings of LNK files and how they can be manipulated to execute malicious code. 📁
-
Exploitation Techniques: Explore various methods to weaponize LNK files, including chaining and using PowerShell scripts.
-
Evasion and Bypasses: Learn how to evade detection by common antivirus solutions and avoid security monitoring tools that are listed on VirusTotal. 🔍
-
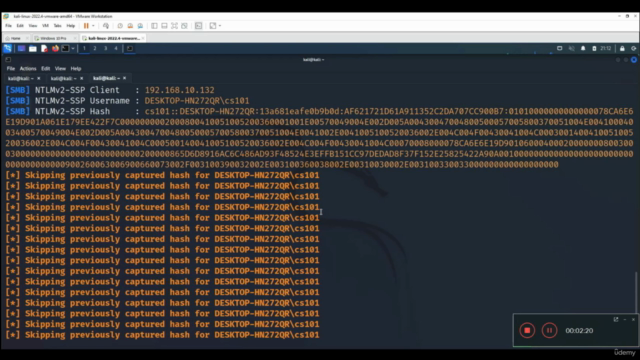
Meterpreter Shell Abuse: Discover how to pivot and maintain access using the Meterpreter shell, a favorite tool among penetration testers for post-exploitation.
-
Reverse Shell Techniques: Understand how to establish a reverse shell from an LNK file to interact with your command and control infrastructure. 🔫
-
Lab Exercises: Put your skills to the test in our hands-on labs, where you can safely experiment with your newfound knowledge.
Who Should Take This Course?
This course is designed for:
- Red Team members looking to enhance their toolkit.
- Penetration testers aiming to expand their techniques.
- Ethical hackers eager to learn and apply modern exploitation methods.
- Cybersecurity professionals who want to understand the threats posed by LNK files.
What's Inside:
- In-depth lecture content covering the theory behind LNK file exploitation.
- Step-by-step guides for setting up your lab environment.
- Practical labs that allow you to apply what you've learned in a controlled, safe environment.
- Access to exclusive resources and tools used by professional Red Teams and penetration testers. 🛠️
Join Us on This Journey:**
Embark on a journey to master the art of weaponizing Windows shortcut (LNK) files with P Ahmad, a seasoned expert in the field of Red Team operations and penetration testing. Sign up for this course today and take your cybersecurity skills to the next level! 🌟
Enroll Now and Transform Your Cybersecurity Career! 🚀💫
Course Gallery

Loading charts...