Planning and Implementing a Security Incident Response

Why take this course?
🚀 Course Title: Planning and Implementing a Security Incident Response
🎓 Course Headline: Learn all about planning and implementing a Security Incident Response along with best practices and recommendations! 🛡️
Course Description:
Embark on a comprehensive journey through the complex landscape of security incident response. In this course, you'll master the critical steps to effectively manage an enterprise-level security incident, steering clear of common pitfalls and significantly enhancing both the effectiveness and efficiency of your response strategies. 🕵️♂️✨
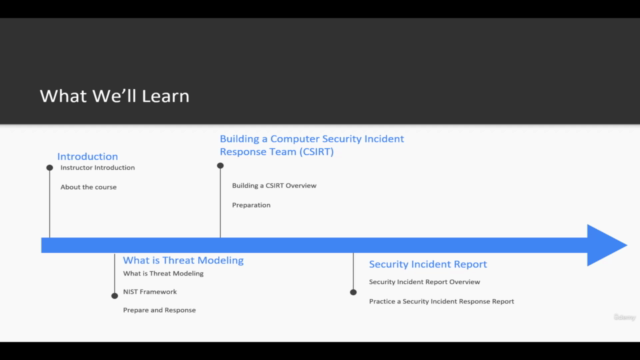
Upon completing this course, you will:
-
Prioritize Effectively: Learn how to assess and prioritize responses to different types of security incidents, ensuring a strategic and calculated approach.
-
Build Your Team: Gain insights into creating an effective computer security incident response team (CSIRT), with a clear understanding of roles, responsibilities, and communication protocols.
-
Action Plan Development: Develop an actionable incident response plan tailored to your organization's unique needs and preparedness level.
-
Post-Incident Activities: Understand the post-incident phase, including investigation, analysis, reporting, and implementing lessons learned to fortify your defenses against future incidents.
Course Offerings:
-
Engaging Video Lectures: Dive into each topic with detailed explanations, real-world examples (and where applicable, live demonstrations) to solidify your understanding. 🎬
-
Interactive Quizzes: Reinforce your learning through review questions at the end of each section, ensuring you grasp the material before moving on.
-
Final Exam: Test your knowledge on the topics and concepts covered in the course with a comprehensive final exam. 🎓
-
Exclusive Resources: Access links to official Microsoft resources, blogs, and videos for additional documentation and insights. 🔗
As part of our comprehensive Microsoft Cyber Security Professional track, this is the 9th course in a series of 9 meticulously crafted courses that cover all facets of cyber security with a focus on Microsoft technologies. This track is designed to equip you with the knowledge and skills necessary to become a successful cyber security professional, covering a wide range of Microsoft security technologies including:
- Microsoft Defender Suite
- Office 365 security features and services
- Microsoft Graph
- Azure Active Directory Security
- And more!
Important Notes:
-
This course is not an official Microsoft program, nor does it represent any endorsement from Microsoft Corporation. 📝
-
Microsoft, Windows, Microsoft 365, and Microsoft Azure are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries.
Join us on this enlightening path to cyber security excellence with Planning and Implementing a Security Incident Response and take your first step towards becoming a certified Microsoft Cyber Security Professional! 🚀💻🔐
Course Gallery


Loading charts...