Penetration Testing for beginners (Hands-on)

Why take this course?
🛡 Start Your Cybersecurity Adventure Today!
Welcome to the Penetration Testing for Beginners Course! 🚀
Are you ready to step into the world of cybersecurity and become an ethical hacker? Our comprehensive 👉 Penetration Testing for Beginners (Hands-on) 👈 course is your ultimate guide to mastering penetration testing using Kali Linux. Whether you're a complete novice or looking to refine your skills, this course will take you from the ground up, transforming you into an expert ethical hacker by the end!
Course Highlights:
- No Prior Knowledge Required: This is the perfect starting point if you're new to penetration testing and ethical hacking.
- Practical and Theoretical Approach: We blend hands-on experience with foundational knowledge to ensure you understand both the methods and the logic behind them.
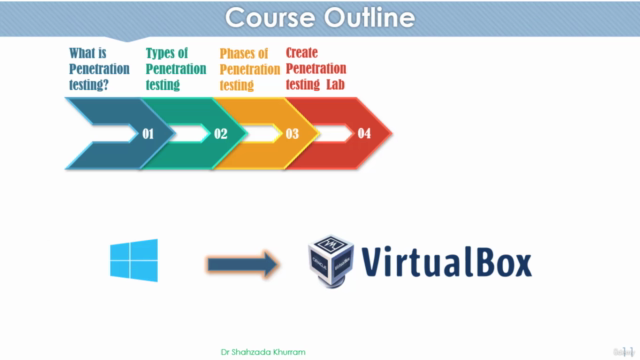
- Lab Environment Mastery: Learn how to set up your very own penetration testing lab, including VirtualBox, Kali Linux, Metasploitable2, and Windows 10.
- Full Penetration Testing Lifecycle Coverage: From information gathering to gaining access, maintaining your presence, clearing logs, to generating final reports, you'll learn it all!
What You’ll Learn:
🎓 Understanding Penetration Testing
- Why Perform a Penetration Test? Discover the critical importance of penetration testing in cybersecurity.
🔍 Basic Terms and Concepts:
- Vulnerability Assessments vs Penetration Testing: Learn the differences and when to use each approach.
🧪 Types of Penetration Testing:
- Based on knowledge of the target, the position of the tester, and where it is performed.
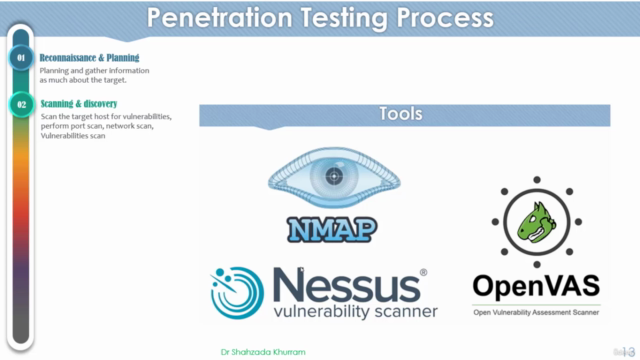
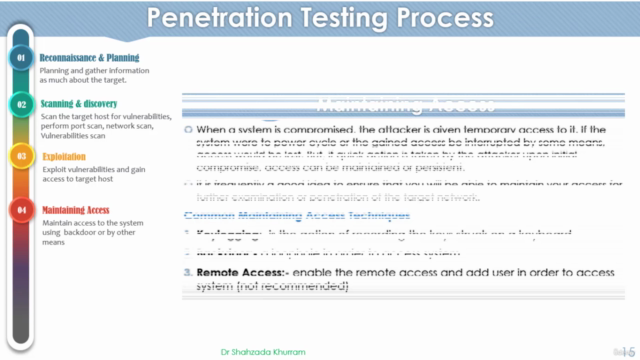
🛠️ Penetration Testing Process Steps:
- A detailed walkthrough of the penetration testing process, ensuring you understand each phase from start to finish.
👨💻 Lab Scenarios:
- Engage with real-world scenarios using Metasploitable2 and Windows 10 targets to apply your skills in a safe, controlled environment.
✨ Exploitation Techniques:
- Explore various ways to exploit common services and vulnerabilities in systems, from FTP to VNC to BindShell.
🧮 Maintaining Access:
- Learn how to establish backdoors and other methods for staying undetected in a penetrated system.
🚫 Clearing Tracks:
- Discover techniques to cover your tracks after an exploit, ensuring your activities leave minimal trace.
📄 Report Generation:
- Create comprehensive reports detailing the vulnerabilities found and their potential impact on the systems tested.
Why Enroll?
- Industry-Relevant Skills: Equip yourself with practical skills that are in high demand across various industries.
- Real-World Experience: Apply what you learn in a simulated environment, giving you confidence when faced with real-world scenarios.
- Career Advancement: Open up opportunities in cybersecurity roles, where professionals are increasingly needed to protect against cyber threats.
👨💻 Your Instructor: Led by an experienced penetration tester and educator, you'll receive personalized guidance and insights that can only come from real-world application of these skills.
Ready to Embark on Your Cybersecurity Journey? 🌐
Enroll in the Penetration Testing for Beginners (Hands-on) course today and take the first step towards a rewarding career as an ethical hacker! With our expert-led, hands-on approach, you'll be ready to tackle the complexities of cybersecurity and protect systems from potential threats. 🛡️💻
Join us and let's turn your curiosity for cybersecurity into a professional superpower! 🚀🌟
Course Gallery

Loading charts...