OWASP Top 10 2017: Exploit and Mitigation

Why take this course?
Course Title: OWASP Top 10 2017: Exploit and Mitigation Mastery
Course Headline: Web Application Pentesting and Mitigations – Unlock the Secrets of Safe Web Applications! 🛡️✨
Course Description:
Dive deep into the world of web application security with our comprehensive course designed around the OWASP Top 10 2017 list of critical web application security risks. This isn't just a theoretical journey; it's a hands-on, practical exploration where you'll practice each attack on a fully equipped vulnerable web application, Mutillidae 2.
Why Choose This Course?
- Real-World Experience: Get your hands dirty with a live lab environment to practice attacks and mitigations.
- Expert Guidance: Learn from the best practices provided by industry-renowned security experts.
- Up-to-Date Knowledge: The OWASP Top 10 list is regularly updated; we keep you informed with the latest vulnerabilities and exploits.
- Comprehensive Coverage: From setting up your lab environment to mastering exploitation and understanding defenses, this course has it all.
Course Breakdown:
🚀 Getting Started:
- Learn how to set up your very own secure lab environment for practice.
- Understand the importance of ethical hacking and its role in security.
🛡️ Exploring the OWASP Top 10 2017:
- In-depth analysis of each of the ten critical vulnerabilities.
- Real-time demonstrations of how these vulnerabilities can be exploited.
Attack Techniques and Mitigations:
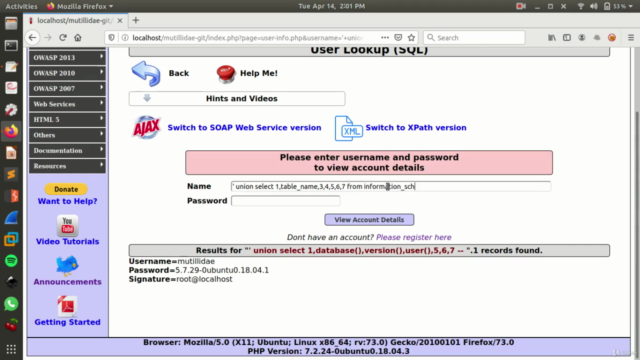
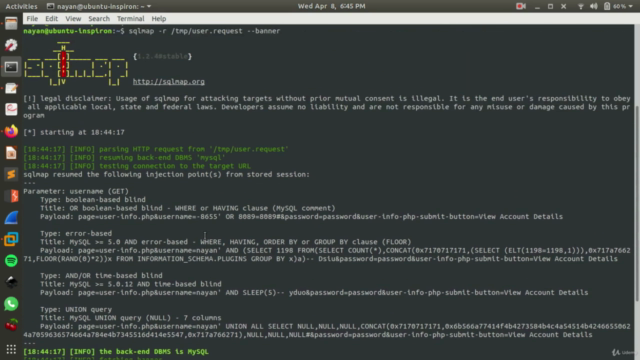
- Injection Attacks (SQL, XPath, Command): Learn to identify and prevent injection flaws.
- Cross-Site Scripting (XSS): Understand the types of XSS and how to protect your web application.
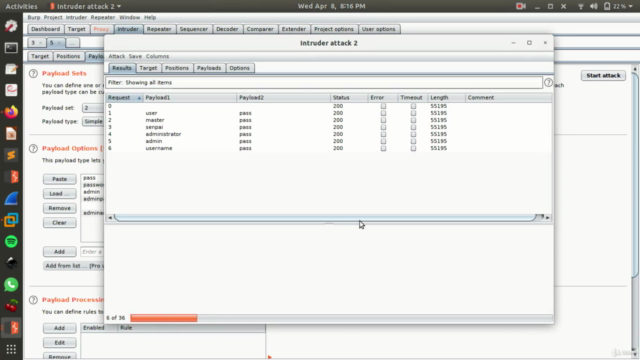
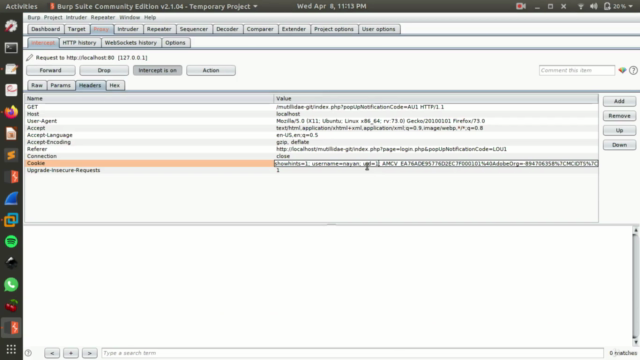
- Broken Authentication: Discover vulnerabilities in session management and authentication.
- Sensitive Data Exposure: Learn how to secure sensitive data, including user data and credentials.
- XML External Entities (XXE): Uncover the risks of XML processing and its consequences.
- Broken Access Control: Explore flaws in access controls that give attackers unauthorized permissions.
- Security Misconfigurations: Identify misconfigured security settings within your web application.
- Cross-Site Request Forgery (CSRF): Understand how CSRF attacks occur and the best ways to defend against them.
- Insecure Deserialization: Learn about the dangers of untrusted input during serialization and deserialization processes.
- Using Components with Known Vulnerabilities: Ensure all third-party components are up-to-date and secure.
- Insufficient Logging & Monitoring: Implement comprehensive logging to detect malicious activities early on.
🎯 Mitigation Strategies:
- Secure Source Codes: Learn from code examples that demonstrate how to avoid vulnerabilities.
- Best Practices: Understand the industry's best practices for securing web applications and why they matter.
Who Should Take This Course?
- Security Professionals: Ethical hackers, penetration testers, and security analysts looking to stay current with industry standards.
- Developers: Web developers who want to understand and prevent vulnerabilities in their code.
- Students: Those studying cybersecurity and aiming to specialize in web application security.
What You Will Gain:
- A thorough understanding of the OWASP Top 10 2017 and how to protect against these vulnerabilities.
- Practical experience in setting up a secure lab environment and exploiting vulnerabilities.
- Knowledge of best practices in writing secure code for web applications.
- The ability to identify and mitigate security threats in real-time, keeping your users and data safe from cyber attacks.
Embark on your journey to mastering web application security with our OWASP Top 10 2017 course today! Let's secure the internet together! 🌐💪
Course Gallery
Loading charts...