Infrastructure & Network: Bug Bounty and Penetration Testing

Why take this course?
🧙♂️ Course Title: Infrastructure & Network: Bug Bounty and Penetration Testing
🚀 Headline: Learn how to hack networks and web applications like black hat hackers, and learn how to secure them from these hackers!
Welcome to the World of Cybersecurity! 🔐
As a beginner with no prior knowledge of penetration testing or hacking, this course will transform you into a cybersecurity expert. Dive deep into the practical and theoretical aspects of penetration testing, learning the tools, methodologies, and techniques used by professionals to secure networks and applications against malicious attacks.
Course Overview:
This is a comprehensive step-by-step guide that starts from scratch. You'll begin by setting up your own lab environment to practice securely and ethically. Here's a glimpse into what you'll learn:
🎯 Core Topics of the Course:
-
Introduction to Ethical Hacking, Footprinting, and Reconnaissance 🔍
- Master the art of gathering essential information about your target server.
- Discover DNS servers, open ports, services, unpublished directories, and sensitive files.
-
Scanning Networks, Enumeration, and Vulnerabilities & System Hacking 🛠️
- Learn to identify and exploit a variety of vulnerabilities.
- Each vulnerability is covered in detail: from understanding what it is to learning how to exploit it.
-
Sniffing Techniques 📡
- Capture encrypted and unencrypted data, including passwords over HTTP, telnet, HTTPS, and more.
-
Metasploit Framework 🛠️
- Utilize this powerful tool to exploit numerous vulnerabilities and create backdoors.
-
Trojans, Backdoors, Viruses, and Worms 🤐
- Understand the impact and mechanisms of these malware types.
-
Cryptography 🔑
- Explore the science of secure communication in the digital world.
-
Penetration Testing on Wireless Networks 📶
- Learn to test and secure wireless networks against unauthorized access.
-
General Penetration Testing 🛡️
- Apply a wide range of techniques to identify and exploit vulnerabilities in various systems.
🎉 Key Takeaways:
- Hands-On Experience: Practical exercises will help you understand the real-world implications of security threats and vulnerabilities.
- Lab Environment: All attacks are performed in a controlled, isolated environment to ensure ethical practices.
- Comprehensive Learning: Covering both theoretical and practical aspects, this course ensures you have a holistic understanding of penetration testing and ethical hacking.
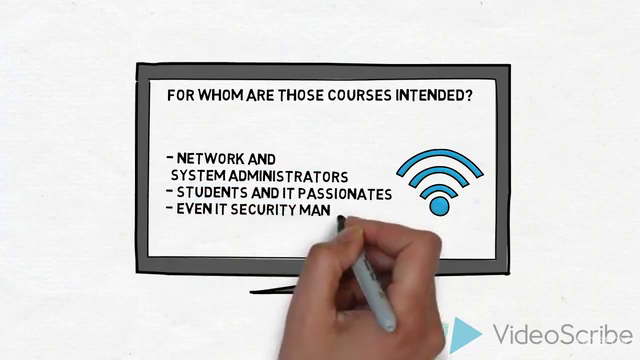
🎓 Who Should Take This Course?
This course is designed for anyone interested in learning about cybersecurity, network security, penetration testing, and ethical hacking. It's ideal for:
- Security Professionals
- Ethical Hackers
- IT Managers
- Network Administrators
- College Students (Computer Science, Cybersecurity)
- Anyone with an interest in cybersecurity and network security
📅 Course Timeline:
This self-paced course is designed to be completed over a 4-6 week period, depending on your commitment and prior knowledge.
👩💻 Get Started Today! Join Gabriel Avramescu in this exciting journey into the realm of cybersecurity. Protect yourself against hackers by learning how they think and act. Enroll now to secure your digital assets and gain a competitive edge in the field of network security.
Remember, knowledge is power, especially when it comes to protecting information systems from attacks. Let's begin this adventure into the world of ethical hacking and penetration testing! 🌐✨
Course Gallery



Loading charts...
Comidoc Review
Our Verdict
This Infrastructure & Network: Bug Bounty and Penetration Testing course by Gabriel Avramescu presents a holistic dive into various network security domains. With engaging presentations and instructive assault breakdowns, learners gain an informative experience in implementing penetration testing on their infrastructure or other systems within the network. Some topics may have become outdated, as it is a 2014 course, but overall, its extensive range of subjects provides beginners with a solid foundation for understanding and safeguarding networks.
What We Liked
- The instructor thoroughly explains every step and attack, making the course easy to follow for beginners.
- Covers an extensive range of topics from port scanning to wireless network hacking, providing a comprehensive learning experience in penetration testing and bug bounty hunting.
- Instructor's knowledgeable and engaging approach effectively captures the audience's attention throughout the course, maintaining enthusiasm and motivation.
- Divided into short learning segments, this organization strategy helps with absorbing content more efficiently and allows for more flexible pacing.
Potential Drawbacks
- The video-only format may be limiting in some instances, as having additional visual aids to support the practical applications could strengthen understanding.
- Some topics can be quite advanced and might require prior familiarity with concepts or tools related to network administration.
- A few reviews indicate that although clear, certain parts of the course are not as engaging for advanced learners.
- As this is an older course (updated in 2024), some tools and techniques discussed may have changed over time, so users should cross-reference with updated resources.