Network Ethical Hacking for beginners (Kali - Hands-on)

Why take this course?
🎉 Network Ethical Hacking for Beginners (Kali - Hands-on) 🔒
Headline: Learn How Hackers Think! & Secure Your Systems Like Security Experts
Course Overview
Welcome to the Network Ethical Hacking course! 🚀 This is your gateway into the world of cybersecurity and ethical hacking. With this course, you will embark on a journey to understand the intricacies of network security from scratch. Whether you're an absolute beginner or have some familiarity with Linux, this course is designed to guide you through the process of mastering ethical hacking using Kali Linux—the most popular penetration testing platform.
🌏 Available in Multiple Languages: This course offers subtitles in English, Spanish, Arabic, Turkish, Russian, French, Chinese, and German, making it accessible to a global audience!
Your Hacking Journey Awaits!
No Prior Knowledge Required 🎓
You don't need any prior knowledge of hacking or Linux to enroll in this course. By the end of it, you will be proficient in hacking systems like a seasoned professional and equipped with the skills to keep yourself secured against cyber threats!
Hands-On Practical Learning 🛠️
This course combines practical hands-on experience with essential theoretical knowledge. We'll start with Kali Linux basics, get you comfortable with the Linux environment, and then proceed to install the necessary software as virtual machines. This is where your ethical hacking adventure begins!
Course Structure 📚
The course is meticulously divided into five comprehensive sections:
- Introduction - Laying the foundation for your hacking journey.
- Pre-Attack Phase - Planning and preparation before launching any attacks.
- Attack Phase - Executing attacks on networks and systems.
- Post-Attack Phase - What to do after an attack has been conducted.
- How to Keep Yourself Protected - Learning how to defend against the attacks you've just learned.
What You Will Learn 🎯
Taking Your First Steps in Ethical Hacking:
- Setting up your penetration testing lab.
- Getting familiar with Kali Linux and its essential commands.
- Mastering Linux commands and the terminal interface.
- Changing your system's MAC address to maintain anonymity.
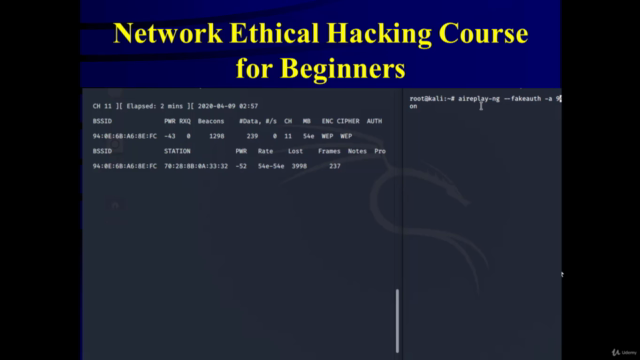
- Wireless network hacking: detailed information about target networks, SSID, encryption types, and more.
- Gaining access to clients connected to a target network without needing the router password.
- Performing various attacks like word list attacks to retrieve passwords.
- Fake authentication attacks targeting routers.
- De-Authentication attacks on routers with no prior knowledge of the password.
- ARP spoofing to become the 'Man in the Middle' (MITM) and intercept data.
- Identifying devices connected to a network you've compromised.
- Scanning networks for detailed information about connected devices.
- Intercepting network traffic.
- Utilizing tools, tricks, and techniques for network hacking.
- Creating your own viruses and hiding them in various file types.
- Gaining remote computer access.
- Hacking Mic, Camera, and Keyboard (Key Logger) capabilities.
- Plus, much more on network hacking!
Staying Secure:
- Learning how to protect yourself against the attacks you've just learned.
Course Highlights 🌟
- Hands-On Experience: Apply what you learn in real-time with practical exercises.
- Comprehensive Coverage: From setting up your lab to mastering post-attack protocols, this course covers it all.
- Multi-Language Support: Engage with the content in the language you're most comfortable with.
Important Notes ☓
- Educational Purpose Only: This course is intended for educational purposes and should only be applied in legal settings, such as your own lab or with explicit permission.
- Course Ownership: This course is exclusively created by Mohammad Hamza Sheikh and is not associated with any other organization. You will receive a Course Completion Certification from Udemy upon finishing the course.
Kind Regards,
Hamza 👋
Get ready to dive into the fascinating world of cybersecurity and ethical hacking! Enroll in "Network Ethical Hacking for Beginners (Kali - Hands-on)" today and transform your skills from zero to hero! 🚀🔐
Course Gallery


Loading charts...
Comidoc Review
Our Verdict
As one of the more comprehensive beginner courses on wireless network ethical hacking with Kali Linux, this 3.5-hour Udemy course focuses primarily on teaching foundational knowledge required for various Wi-Fi attacks. Although somewhat outdated, it distinguishes itself from other similar courses through a more engaging and hands-on approach, covering ARP spoofing, USB adapters, and even keylogger tools. However, the curriculum would benefit from additions like phishing attack instruction, social engineering techniques, and up-to-date content on currently available tools in this fast-paced field. With a moderate overall rating of 4.36 from 211,135 students as of July 2021, prospective learners should expect a valuable but not flawless introduction to hacking wireless networks—ideal for those looking to gauge their interest in infosec or build upon pre-existing fundamental skills.
What We Liked
- Designed for beginners, providing a comprehensive introduction to network ethical hacking concepts and techniques
- Instructs on how to use Kali Linux, including important commands for interacting with the command terminal
- Hands-on approach using virtual machines for practicing attacks in a controlled environment
- Focuses on Wi-Fi networks, covering various types of attacks such as De-Authentication, word list password recovery, and ARP spoofing
Potential Drawbacks
- Course material seemingly outdated, with disparity between some tools presented in the course and their current versions
- Lacks other essential hacking categories like email and social media attacks or bypassing antivirus software
- VM installation time consuming for new users; could be listed as a prerequisite
- Several learners reported minor issues including missing directories, inaccuracies, and difficulties setting up certain tools