MITRE TRAM: Mapping Threat Reports to ATT&CK
Why take this course?
Master Threat Intelligence with MITRE TRAM: Your Journey to Mapping Reports to ATT&CK Starts Here! 🚀
Course Title: Unlocking Insights: MITRE TRAM and ATT&CK Mapping
Instructor: Vipul Dabhici
Course Description: TRAM, or Threat Report ATT&CK Mapper, is a groundbreaking web-based tool that revolutionizes the way we handle cyber threat intelligence. It automates the extraction of adversary behaviors and maps them to the MITRE ATT&CK framework. As an open-source platform, TRAM stands at the forefront of research into automating this critical process. This course will guide you through the intricacies of using TRAM to test and refine Machine Learning models for identifying ATT&CK techniques in threat intelligence reports. You'll learn how to train ML models, validate their results, and ultimately contribute to a more robust and accurate integration of ATT&CK within the cybersecurity community. 🛡️
What You Will Learn:
- Understanding TRAM: Discover how TRAM works and its significance in automating the mapping process.
- Data Management: Master the steps involved in getting, cleaning, and preparing data for analysis.
- Model Training: Learn to train models effectively to recognize ATT&CK techniques within threat reports.
- Report Uploading and Analysis: Get hands-on experience with uploading reports and testing data through ML models.
- Evaluating and Refining: Understand how to accept or review model decisions based on scores and identified techniques.
- Feedback Loop: Utilize the feedback loop to continuously improve the accuracy of ATT&CK mappings.
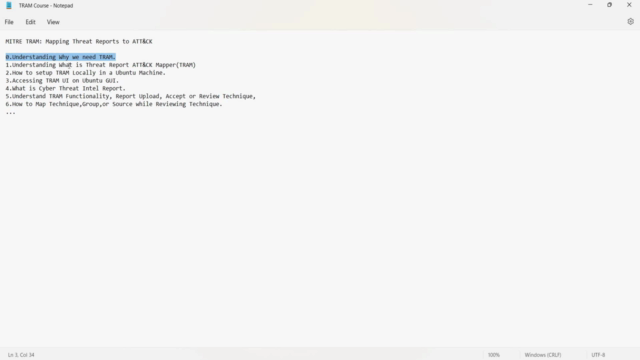
TRAM's Role in Threat Intelligence:
- Ease of Use: TRAM makes it simpler for analysts to integrate ATT&CK into their products, reducing the complexity and time involved.
- ATT&CK Mastery: With over 266 techniques and an ever-evolving framework, TRAM helps you manage the complexities of remembering every technique.
- Actionable Reporting: Learn how to effectively use reporting features within TRAM to enhance your threat intelligence processes.
Why Enroll in this Course?
- Practical Skills: Gain hands-on experience with a real-world tool that is shaping the future of cyber threat intelligence.
- Community Engagement: Join a community of professionals committed to advancing the understanding and application of ATT&CK.
- Stay Ahead: Keep up with the latest developments in cybersecurity by learning how to use cutting-edge tools like TRAM.
Course Outline:
- Introduction to TRAM: An overview of what TRAM is and why it's a game-changer for threat intel analysis.
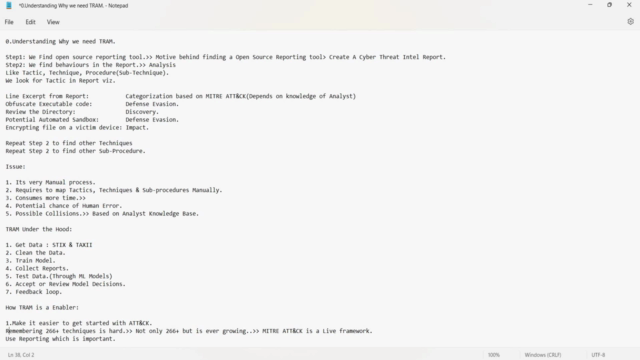
- Data Acquisition: Explore how STIX & TAXII protocols feed into the TRAM ecosystem via Tip (Trustworthy Internet-based Protocol).
- Data Preparation: Learn best practices for cleaning your data to ensure accurate ATT&CK mappings.
- Machine Learning Models: Understand the process of training and testing ML models to identify ATT&CK techniques in prose.
- Report Uploading Process: Get step-by-step instructions on uploading threat reports for analysis.
- Decision Validation: Learn how to evaluate model decisions based on their scores and the ATT&CK techniques identified.
- Continuous Improvement: Engage in the feedback loop to refine your ML models and enhance the accuracy of ATT&CK mappings.
Ready to Master Cyber Threat Intelligence with TRAM? Enroll Now and Transform Your Analytical Skills! 🌟
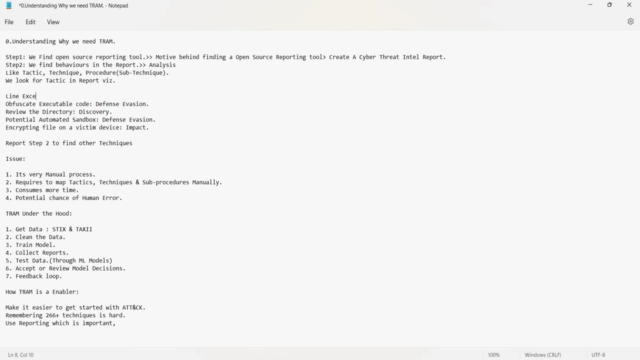
Dive Deeper: Inside TRAM's Architecture:
- Get Data: STIX & TAXII data sources lead to valuable insights through the Tip protocol.
- Clean the Data: Ensure data quality for precise ATT&CK technique mapping.
- Train Model: Develop and hone your ML models to recognize patterns in threat reports.
- Collect Reports: Upload and handle various report types efficiently.
- Test Data: Apply ML models to test and validate their effectiveness in identifying ATT&CK techniques.
- Model Decisions: Make informed decisions on the results of your ML model tests with a clear understanding of scores and techniques identified.
- Feedback Loop: Embrace the iterative process of refining your approach for better, more accurate outcomes. 🔄
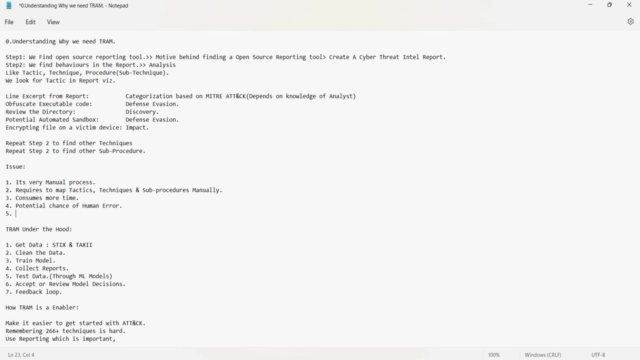
Empower Your Threat Intelligence Practice:
- Simplify ATT&CK Integration: Discover tools and techniques to easily incorporate ATT&CK into your analysis.
- Overcome Technique Overload: Learn strategies to manage the vast array of ATT&CK techniques, ensuring you keep pace with an evolving framework.
- Leverage Reporting Capabilities: Maximize the value of your threat intelligence efforts through effective reporting and documentation.
Join us on this journey to demystify cyber threat intelligence with TRAM and ATT&CK! Sign up today and become a certified expert in mapping threat reports to MITRE ATT&CK. 🛡️📈
Enroll now and embark on your journey to becoming a proficient user of the MITRE TRAM tool, mastering the art of mapping Threat Reports to the MITRE ATT&CK framework. This course is your gateway to elevating your cybersecurity threat intelligence capabilities! 🚀✨
Course Gallery
Loading charts...