Misconfigurations Management

Why take this course?
🛡️ Master Misconfigurations with "Misconfigurations Defense for Red and Blue Teams" 🚀
Course Overview: This comprehensive course is tailored for cybersecurity enthusiasts, Red & Blue Teamers, network defenders, GRC professionals, and anyone looking to enhance their security posture. With a focus on understanding common misconfigurations that pave the way for cyber attacks, you'll learn how to prevent these vulnerabilities in both cloud and on-premises environments. 🌩️🛡️
Why Take This Course?
- Real-World Insights: Learn from top misconfigurations identified by NSA and CISA experts during security assessments across various organizations.
- Practical Skills: Transition your knowledge into actionable skills to defend against cyber attacks effectively.
- Holistic Understanding: Gain a comprehensive view of how Red and Blue Teams can work synergistically for robust network defense.
Course Highlights:
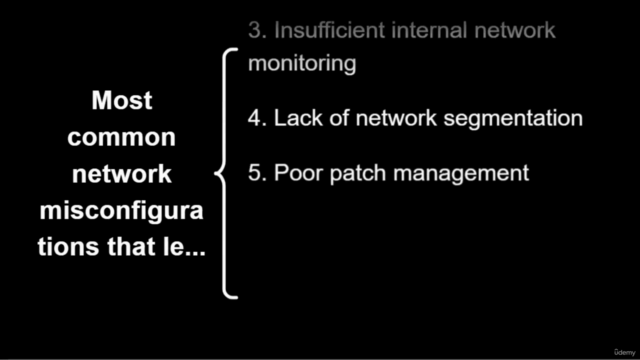
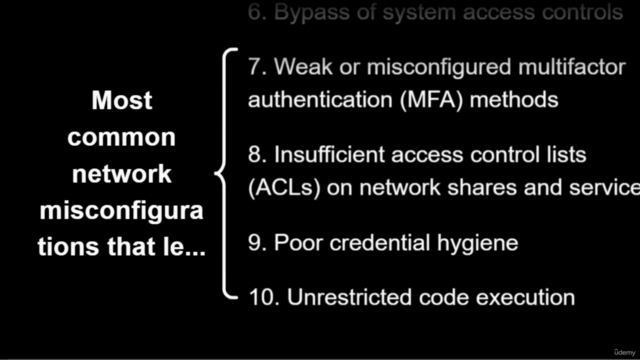
🏆 Top 10 Misconfigurations Covered:
- Default configurations of software and applications
- Improper separation of user/administrator privileges
- Insufficient internal network monitoring
- Lack of network segmentation
- Poor patch management
- Bypass of system access controls
- Weak or misconfigured multi-factor authentication (MFA) methods
- Insufficient access control lists (ACLs) on network shares and services
- Poor credential hygiene
- Unrestricted code execution
🔒 Understanding the Risks:
- Explore how each of these misconfigurations can be exploited by attackers.
- Learn about the cyber risks associated with these vulnerabilities.
🛡️ Mitigation Strategies:
- Discover best practice recommendations for mitigating these cyber risks.
- Utilize MITRE ATT&CK framework to understand and counteract techniques leading to misconfigurations.
📊 Tools & Techniques:
- Get introduced to open-source tools for configurations management to mitigate cyber attacks.
- Improve monitoring and hardening of networks with actionable advice for Blue & Network Admin Teams.
🤖 Embracing AI:
- Learn how AI can assist in generating defense checklists tailored for network defenders.
🌫️ Securing Your Cloud (Azure):
- Engage in Azure Penetration Testing to secure your cloud environment from misconfigurations.
Course Benefits:
- Root Cause Analysis: Introduction to the practice of root cause analysis and its significance in developing a cybersecurity mindset.
- Practical Application: Learn how to apply concepts in real-world scenarios, ensuring you're prepared to tackle misconfigurations in your environment.
- Community Knowledge: Leverage insights from the broader cybersecurity community to stay ahead of emerging threats and vulnerabilities.
Who Should Take This Course?
- Aspiring cybersecurity professionals
- Red Teamers looking to enhance their attack surface identification skills
- Blue Teamers aiming to strengthen network defenses
- Network administrators responsible for securing cloud environments
- Security leaders seeking a holistic understanding of both offensive and defensive strategies
- GRC professionals interested in aligning governance with cybersecurity best practices
Enroll now to fortify your knowledge against the most common cybersecurity misconfigurations and emerge as a guardian of digital safety! 🔒📚💪
Course Gallery

Loading charts...