Mastering Command Injection - The Ultimate Hands-On Course

Why take this course?
🎉 Mastering Command Injection - The Ultimate Hands-On Course 🛡️
GroupLayout: David Bombal
Discipline: Ethical Hacking, Software Development, Penetration Testing
Course Headline:
"How to Find, Exploit and Defend Against Command Injection Vulnerabilities"
Course Description:
🔒 Understanding Command Injection:
Command injection is a potent attack vector that can lead to full system compromise. In this course, we delve into the intricacies of command injection vulnerabilities, which allow an attacker to manipulate an application into executing arbitrary commands on the underlying operating system. This often results in unauthorized access and potentially complete remote code execution, making it a high-priority target for attackers.
Key Learning Objectives:
-
Detection Techniques:
Learn how to detect command injection vulnerabilities from both black-box (external) and white-box (internal) perspectives. -
Exploitation Methods:
Gain a deep understanding of the various methods for exploiting command injection vulnerabilities effectively. -
Preventive Measures:
Understand the critical steps to take in order to prevent command injection attacks, including secure coding practices and application design principles.
Practical Experience:
-
Hands-On Labs:
Engage in five comprehensive labs designed to provide you with practical experience in identifying, exploiting, and defending against command injection vulnerabilities. These labs range from introductory to complex scenarios and will help you to:-
Manually exploit command injection vulnerabilities.
-
Automate your attacks using Python scripts.
-
Course Features:
-
Beginner-Friendly Content:
We've structured the course content so that it's accessible to beginners, ensuring you won't feel overwhelmed as you learn. -
Real-World Applications:
Apply your new skills through practical labs that simulate real-world scenarios.
Who This Course Is For:
🚀 Ideal for:
- Penetration Testers (ETH)
- Application Security Specialists
- Bug Bounty Hunters
- Software Developers
- Ethical Hackers
- And anyone with a keen interest in web application security!
By enrolling in this course, you'll not only understand the mechanisms behind command injection vulnerabilities but also how to exploit and protect against them. Take the first step towards mastering one of the most critical skills in cybersecurity today!
Enroll Now and Elevate Your Cybersecurity Skills with Expert-Led Training! 🚀🔐
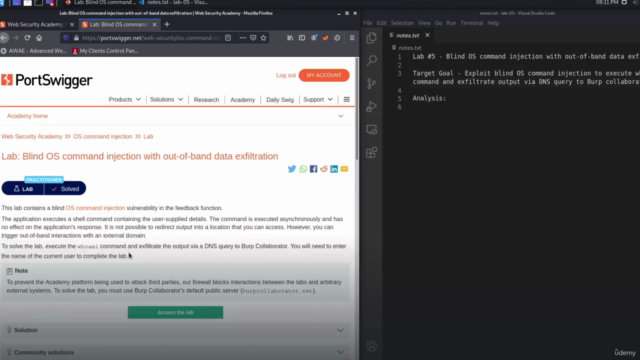
Course Gallery


Loading charts...