Kali Linux Wireless Penetration Testing - Novice to Pro!

Why take this course?
🌟 Course Title: Kali Linux Wireless Penetration Testing - Novice to Pro!
Course Headline:
Unlock the Secrets of Wireless Security with Kali Linux Mastery!
🚀 Course Description: Kali Linux, the #1 security operating system for hackers, is at the forefront of penetration testing. With its robust collection of tools tailored for professional security testing, it's no wonder Kali Linux has become the go-to choice for ethical hackers. As hacker groups have risen to prominence, Kali Linux has been a staple in their arsenal, used to protect and test networks against potential threats.
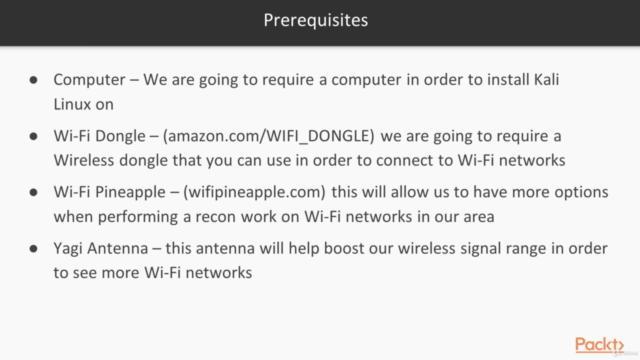
This comprehensive 3-in-1 course is designed as a step-by-step guide through real-world attack scenarios, offering a deep dive into the world of wireless penetration testing techniques. You'll be equipped with a variety of tools to add to your ethical pen testing tool belt, including high-powered antennas, Android devices, and laptops. Learn to search for and reach wireless networks from great distances, and then use cutting-edge tools to uncover hidden wireless networks and crack their passwords.
📚 Contents and Overview: This training program is a treasure trove of knowledge, comprising 3 complete courses that will elevate your skills from novice to professional in wireless penetration testing with Kali Linux:
-
Kali Linux 2017 Wireless Penetration Testing for Beginners:
- Discover the essential products to enhance your ethical pen testing tool belt.
- Utilize high-powered antennas and a variety of tools to connect to wireless networks, even with WEP/WPS/WPA/WPA2 security protocols in place.
-
Kali Linux Penetration Testing Recipes:
- Dive into the world of ethical hacking with Kali Linux.
- Perform comprehensive vulnerability tests on websites and servers.
- Learn to brute-force past passwords, search for backdoors, and create a professional report for your clients.
-
Kali Linux Advanced Wireless Penetration Testing:
- Master the art of testing wireless network security.
- Explore advanced techniques using Kali Linux to find hidden networks and Bluetooth devices.
- Connect, enumerate, and extract information from any wireless-enabled device and network using a range of tools and software programs.
🧑💻 About the Authors: This course is brought to you by industry experts:
-
Aubrey C. Bas�, an experienced programmer who began his journey on a Commodore Vic-20. His programming career has spanned system administration, ethical hacking, website mastery, mobile development, and game development. As an author, speaker, and blogger, Aubrey's passion for information security shines through his contributions to the field.
-
Vijay Kumar Velu, a dedicated information security practitioner with over 11 years of IT industry experience. His expertise as a licensed penetration tester and his multiple security qualifications make him a respected voice in the world of cybersecurity. Vijay's commitment to the community is evident through his roles in organizations like the Cloud Security Alliance (CSA) and the National Cyber Defense and Research Center (NCDRC).
Join us on this journey to master wireless penetration testing with Kali Linux, and take your cybersecurity skills to the next level! 🔐💻
Course Gallery

Loading charts...