JWT Authentication using MERN Stack

Why take this course?
🎉 Course Title: JWT Authentication using MERN Stack
🚀 Headline: Dive into the World of RESTful API Security with JSON Web Token (JWT) on the MERN Stack!
Welcome to the Course on JWT Authentication using MERN Stack! 🧗♂️
What is JSON Web Token (JWT)? 🎫
JSON Web Token (JWT) is a modern and secure way of handling HTTP authentication and information exchange. It's an open standard (RFC 7519) that allows you to transmit claims between parties over HTTP in a compact and self-contained manner. These claims can be verified and trusted because they are signed—digitally!
The Anatomy of JWT:
- Header: Encodes the type of the token (JWT) and the algorithm used for signing the token (e.g., HMAC SHA256, RSA, ECDSA).
- Payload: Contains the claims—user ID, roles, expiration, and so on. It's where the magic happens!
- Signature: Ensures that the sender of the JWT is who they say they are and that the token hasn't been tampered with.
🔍 Deep Dive into JWT Components:
- Header - The compact serialization of JSON data that consists of two parts: the algorithm and the encoded JWT ID.
- Payload - The assertion (a claim) that is being made about the entity (typically, the user) - e.g., user identity, role, permissions, etc.
- Signature - Used to verify that the sender of the JWT is who they say they are and to ensure that the message wasn't changed along the way.
Why Use JWT? 🛡️
- Compact: Easily transmitted through a URL, POST parameter, or inside an HTTP header. Its small size means quick transmission and processing.
- Self-contained: Contains all the user information to avoid unnecessary database calls.
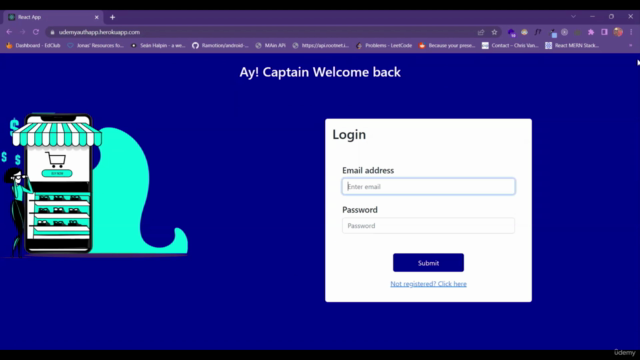
How JWT Works in Authentication:
When a user logs in with their credentials, the server responds by sending back a JWT. This token is a credential for accessing the protected routes of the application. Here's how it works:
- User Logins: The user sends their username and password to the server.
- Server Validates Credentials: If valid, the server generates a JWT token and returns it to the user.
- Token in Use: Each time the user wants to access a protected resource, they send the JWT, usually through the
Authorizationheader with theBearerschema. The content of the header might look like this:Authorization: Bearer <your_jwt_token>.
Key Points to Remember:
- Security: Tokens should be used only as needed and not stored indefinitely.
- No Sensitive Data Storage: Avoid storing sensitive session data in browser storage due to potential security issues.
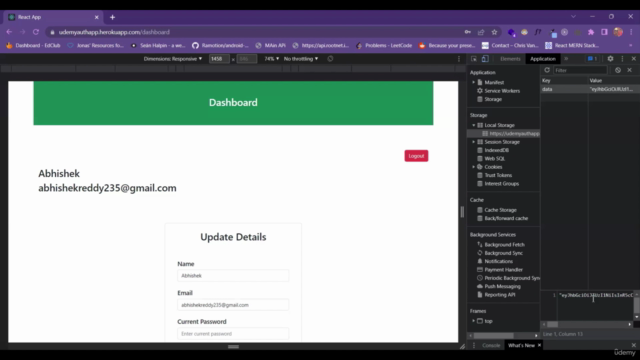
Hands-On with MERN Stack:
In this course, you'll learn how to implement JWT authentication in a MERN stack application (MongoDB, Express.js, React, and Node.js). You'll cover:
- Frontend: Using React to create user interfaces and handle JWTs securely.
- Backend: Setting up Node.js with Express.js to authenticate users and issue tokens.
- Database: Storing and retrieving user data from MongoDB.
- Security Best Practices: Ensuring your application is safe from common security threats.
Get ready to secure your MERN Stack applications with JWT Authentication! 🚀
Course Gallery
Loading charts...