ISO 27001:2013 Information Security Management System - ISMS

Why take this course?
🎓 ISO 27001:2013 Information Security Management System (ISM) - Awareness Course 🛡️
Course Overview:
Embark on a comprehensive journey to understand the ISO 27001:2013 standard, which is pivotal for any business aiming to manage and secure their information assets effectively. This beginner-friendly course serves as an introduction to the standard, providing clear explanations of all the clauses, guiding you through the necessary control measures to ensure compliance, and offering practical examples to illustrate real-world applications.
Why Take This Course?
In the digital age, where businesses are increasingly reliant on electronic information, understanding ISO 27001:2013 is crucial for safeguarding your data. Whether you're a small startup or a large enterprise, this course will equip you with the knowledge to confidently navigate the complexities of information security and to implement a system that stands up to international standards.
Course Benefits:
- Foundational Understanding: Build a solid foundation on ISO 27001:2013 and its role in your business's Quality Management System (QMS).
- Comprehensive Guidance: Follow a structured, clause-by-clause breakdown of the standard, including practical insights for each section.
- Annex A Alignment: Gain detailed knowledge of each control in Annex A, essential for setting up your ISM effectively.
- Practical Application: Learn how to apply what you've learned to prepare documentation, implement controls, and verify your system's effectiveness.
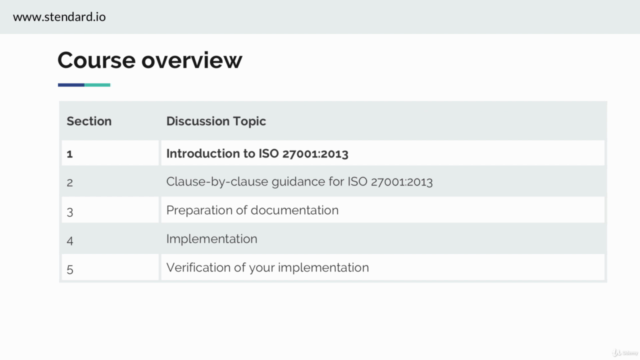
Course Structure:
Section 1: Introduction to ISO 27001:2013
- History and general concepts of the standard
Section 2: Clause-by-Clause Guidance for ISO 27001:2013
- Clause 1 to 3 + Clause 4: Understanding the context of your organization within the ISM framework
- Clause 5: The importance of leadership in shaping information security culture
- Clause 6: Ensuring proper support mechanisms are in place for your ISM
- Clause 7: Operational procedures that align with your information security objectives
- Clause 8: Monitoring, measuring, reviewing, and improving the performance of your ISM
- 🔍 Annex A: Deep dive into understanding and implementing each control within the ISMS framework:
- Information security policies
- Organizational structure
- Human resource security
- Asset management
- Access control
- Cryptography
- Physical and environmental security
- Operations security
- Communications and operations management
- System acquisition, development, and maintenance
- Supplier relationships
- Information security incident management
- Business continuity planning
- Compliance
- 🔍 Annex A: Deep dive into understanding and implementing each control within the ISMS framework:
- Preparation of Documentation: Learn how to prepare and maintain documentation that supports the implementation of your ISM
- Implementation: Steps to successfully implement controls based on Annex A
- Verification of Implementation: Methods to verify that your ISM is operating effectively and continuously improves
Who Should Take This Course?
This course is designed for:
- Information Security Professionals
- IT Managers and Leaders
- Business Owners
- Quality Assurance Personnel
- Anyone responsible for information security within their organization
How to Enroll?
Ready to elevate your understanding of information security management systems? 🚀 Enroll now and take the first step towards ensuring your organization's data is protected according to international standards. Let's secure your information assets together!
Join us on this informative journey and become an expert in ISO 27001:2013. Secure your place today and safeguard your business's future! 🏆
Course Gallery



Loading charts...