Intro to Offensive Security ( Arabic )

Why take this course?
Course Title: Intro to Offensive Security (Arabic) 🚀✨
Course Headline: "Think Like an Attacker: Develop the Skills to Protect Against Cyber Threats" 🔒🛡️
Course Description:
Are you ready to step into the realm of cybersecurity and understand the mind of a cyber attacker? Our "Intro to Offensive Security" course, led by the renowned expert Omar Tercer, is your gateway to mastering the art of defensive strategies through an attacker's lens. 🎓
Why Take This Course?
- Understand the Threat: Learn how cyber attackers think and operate to better anticipate and neutralize threats.
- Skill Development: Acquire essential skills in penetration testing, vulnerability assessment, and system exploitation.
- Hands-On Experience: Engage with practical exercises that simulate real-world scenarios, providing you with the experience you need to tackle actual cybersecurity challenges.
- Secure Your Systems: Gain knowledge on how to protect your own systems from attacks by understanding the methods attackers use to compromise them.
Course Highlights:
- Comprehensive Training: Get a complete introduction to offensive security concepts and techniques in Arabic, making it accessible for Arabic-speaking learners.
- Industry-Relevant Tools: Familiarize yourself with the latest tools used by professionals in the field of cybersecurity.
- Real-World Simulations: Participate in exercises that mirror real-world attack and defense scenarios, allowing you to apply your skills effectively.
- Learn from an Expert: Be guided by Omar Tercer, whose expertise will provide you with insights into the complexities of offensive security.
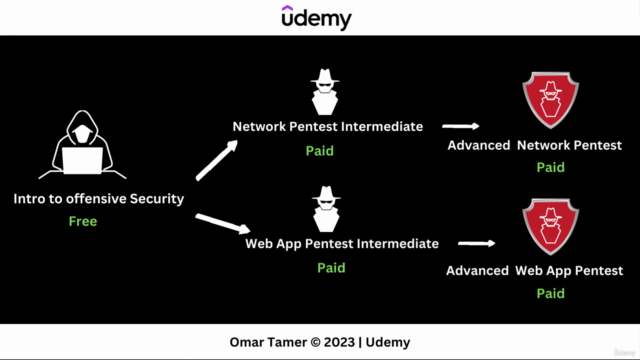
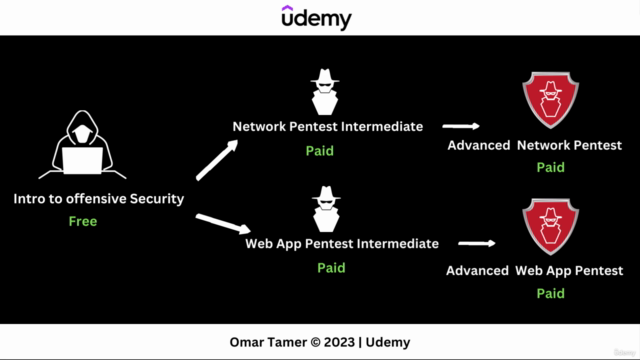
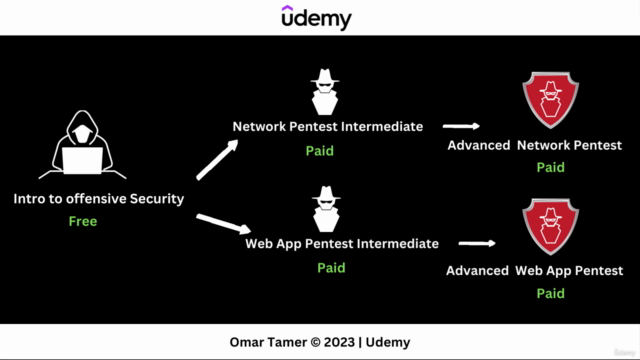
Course Outline:
- Introduction to Cybersecurity: Understand the fundamentals and why they are critical for protecting your systems.
- Penetration Testing: Learn the process of testing your computer system's defenses to find vulnerabilities that an attacker could exploit.
- Vulnerability Assessment: Identify security weaknesses within systems, applications, and networks before they can be exploited.
- Exploitation Techniques: Understand how attacks are carried out and what measures you can take to prevent them.
- Secure Networks: Explore the principles of secure network design and management to minimize risks.
- Web Application Security: Protect your web applications from common attacks, such as SQL injection and cross-site scripting (XSS).
- Wireless Security: Secure your wireless networks against unauthorized access and potential threats.
- Incident Response: Learn how to react effectively to security incidents and reduce their impact on systems.
- Ethical Considerations: Discuss the ethical implications of offensive security practices and the importance of adhering to legal frameworks.
Who Should Take This Course?
- Aspiring Cybersecurity Professionals: If you're looking to start a career in cybersecurity, this course will equip you with a strong foundation.
- IT Security Enthusiasts: For those who have an interest in IT security and want to delve deeper into offensive strategies.
- Security Analysts: Professionals who aim to enhance their understanding of attacker methodologies to better defend against cyber threats.
Join Our Community of Learners! 🌐 Embark on your journey to mastering cybersecurity with a community of like-minded individuals. Engage in discussions, share insights, and collaborate on solving real-world problems.
Ready to think like an attacker and secure your systems against the ever-evolving threat landscape? Enroll now and transform your approach to cybersecurity! 🛡️💪
Course Gallery

Loading charts...