Hacking tutorial: Undetectable Payloads

Why take this course?
🚀 Hacking Tutorial: Undetectable Payloads 🎓
Course Headline: Unlock the Secrets of Ethical Hacking with Our Comprehensive Course on Creating Undetectable Payloads!
Course Description: Are you ready to elevate your hacking skills to the next level? If so, this is the perfect course for you! Whether you're a beginner or an experienced professional looking to refine your craft, our "Hacking Tutorial: Undetectable Payloads" will guide you through the process of crafting your own stealthy payloads. 🛠️✨
Why Take This Course?
- Easy to Follow: Steps and explanations tailored for beginners, making complex concepts approachable.
- Practical Skills: Learn by doing with a hands-on approach to master the art of creating undetectable payloads.
- Professional Growth: Enhance your penetration testing abilities and gain valuable knowledge that can accelerate your growth as a hacker or pentester.
- Real-World Applications: Use your newfound skills to assess security vulnerabilities, conduct research, and help secure organizations against malicious attacks.
What You'll Learn:
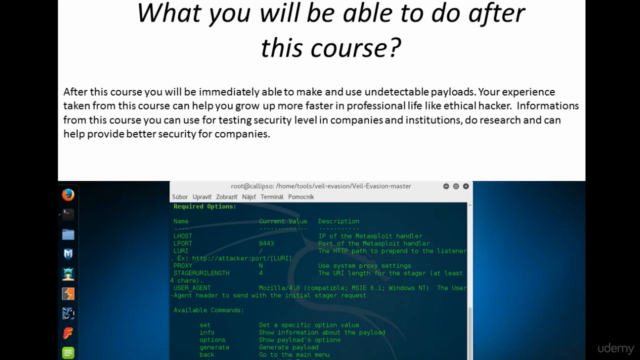
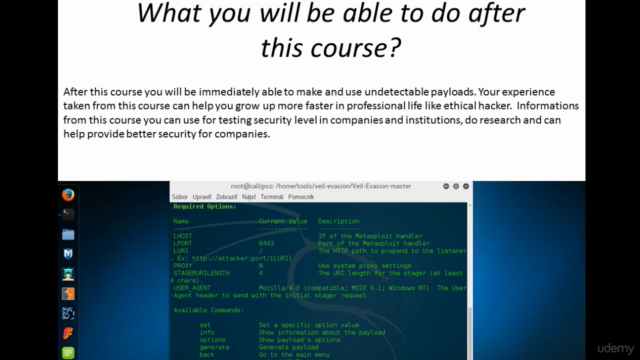
- Program Walkthroughs: We'll explore the capabilities of key programs used in payload creation, including Veil-Evasion, Veil-Ordnance, Winpayloads, Shellter, and msfconsole.
- Virtual Environment Setup: Step-by-step instructions on setting up a VirtualBox VM with Kali Linux 2016.1 for a safe and controlled learning environment.
- Practical Use of Tools: Hands-on experience with the installation and basic use of essential tools for payload generation.
Course Breakdown:
- Understanding Payload Creation: Learn the fundamentals of payload development, including how they work and why they are undetectable.
- Program Installation and Configuration: Get your environment ready with detailed instructions on setting up all necessary tools.
- Payload Development: Dive into creating your first payload using Veil-Evasion and other powerful tools, learning how to evade antivirus software along the way.
- Injection Techniques: Discover how to inject payloads into executable programs to achieve your desired outcome.
- Real-World Application: Apply your skills to perform penetration testing or enhance security measures in a professional setting.
By the end of this course, you'll not only understand how to create undetectable payloads but also how to apply them ethically and responsibly. With the knowledge gained here, you'll be well on your way to becoming an expert in the field of ethical hacking and penetration testing. 🔐💪
Join us today and take the first step towards mastering ethical hacking and payload creation!
Course Gallery
Loading charts...