Hacking with HID Devices v1.0

Why take this course?
🔐 Unlock the Secrets of HID Attacks with "Hacking with HID Devices v1.0" 🚀 betray no fear – delve headfirst into the clandestine world of Hardware Interface Device (HID) hacking, where everyday inputs can become gateways to unauthorized system access. This isn't just any old course; it's your key to unlock the mysteries of HID attacks, complete with practical examples and real-world scenarios that will challenge and expand your cybersecurity acumen.
Course Title: 🖥️ Hacking with HID Devices v1.0
Course Headline: 🛡️ Build your skills and knowledge of HID attacks with practical examples and real-world scenarios.
Why Take This Course?:
- Understand the Fundamentals: Learn how HID attacks work, their significance in modern cybersecurity, and the vulnerabilities they exploit.
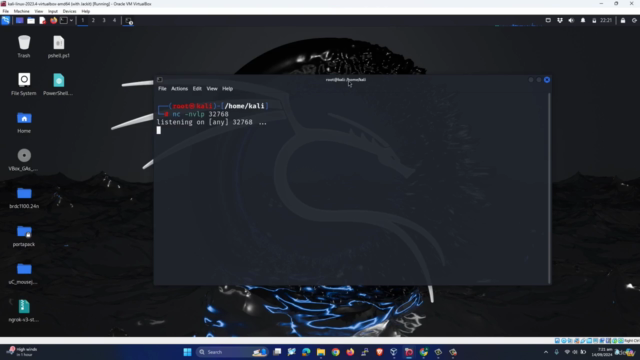
- Real-World Application: Transition from theory to practice by working with devices such as DigiSpark, BadUSB (Arduino Micro), Cactus HID, and Raspberry Pi Pico.
- Configure & Use HID Devices: Get hands-on experience in setting up these devices for executing a variety of crafty attacks – from keystroke injections to command execution on remote servers.
- Hands-On Learning: Follow step-by-step guidance to configure and use HID payloads effectively, ensuring you learn by doing.
- Expert Instructor: Be mentored by course instructor Arsalan Saleem, an expert in the field with a wealth of knowledge to share.
What You'll Master:
- Reverse Shell Techniques: Gain command over target systems through advanced reverse shell methods without raising any alarms.
- Deploying Scripts: Learn how to install and utilize necessary tools, set up your environment, and run scripts for ethical hacking.
- Ethical Hacking Toolkit: Expand your toolkit with techniques that are crucial for ethical hackers targeting hardware vulnerabilities.
- Real-World Defense Mechanisms: Understand how to protect systems from HID-based attacks and recognize the risks these devices pose in a real-world setting.
Who Should Take This Course?
- Beginners & Hobbyists: If you're new to the field, this course will give you a solid foundation of knowledge and hands-on skills.
- Security Enthusiasts: For those interested in cybersecurity, this course will enhance your understanding of hardware-based security threats.
- Experienced Professionals: Ethical hackers and cybersecurity experts will gain advanced techniques to add to their repertoire.
- Defense Analysts & DevOps Engineers: Learn to identify and mitigate HID-related risks within your infrastructure.
By the End of This Course, You Will Be Able To:
- Confidently apply HID attack techniques in ethical hacking scenarios.
- Understand the critical aspects of defending against HID-based attacks.
- Protect systems from unauthorized access through trusted hardware devices.
🎓 Join "Hacking with HID Devices v1.0" and elevate your cybersecurity game today! 🌐
Don't just take our word for it – check out the course outline, syllabus, and instructor profile to see everything that this comprehensive course has in store for you. With expert-led instruction, a focus on hands-on application, and a commitment to equipping learners with the skills needed to succeed, there's no better time to start your journey into HID hacking. Enroll now and become a master of HID attacks! 🛠️💻
Course Gallery

Loading charts...