Ethical Hacking: Weaponization

Why take this course?
TDM Course Description ---
Course Title: Ethical Hacking: Weaponization with Office Documents
Course Instructor: Peter Acourse
Unlock the World of Ethical Hacking! 🔐✨
Course Headline: Master the Art of Offensive Security! 🚀
Are you fascinated by the world of cybersecurity and eager to understand how hackers can turn everyday office documents into weapons? This course is your gateway into the realm of Ethical Hacking, where you'll learn the intricacies of compromising systems using office documents and HTML applications.
Course Description:
Understanding the Cyber Threat Landscape 🌐
Hackers are not just about breaking into systems; they can be master manipulators who wish to maintain covert access for their own purposes. Learn how Trojan horses, rootkits, and other malicious files can be used to keep an unauthorized backdoor open in a target system. Discover the tactics that attackers use to stay hidden and achieve their objectives undetected.
The Importance of Vigilance in Cybersecurity 🛡️
Cyber attacks are more than just a technical challenge; they represent a significant threat to data integrity, privacy, and security. In this course, you'll understand the cyber kill chain and how each step can expose vulnerabilities within your network. Gain insight into how to detect and prevent these threats before they escalate.
Hands-On Learning: Hacking with Office Documents 📄
- Creating a Reverse Shell via Office Document: Learn to craft an office document that, when opened by the victim, will execute a reverse shell, giving you access to their system.
- Exploiting Microsoft Office Applications: Dive into the world of exploiting vulnerabilities within Microsoft Office to achieve code execution on a target machine.
Discovering the Power of HTML Application Hacking 🌐
- HTML & Web Hacking Fundamentals: Understand how web applications can be manipulated to execute malicious code.
- Exploiting Cross-Site Scripting (XSS): Learn to identify and exploit XSS vulnerabilities to perform actions on behalf of the victim.
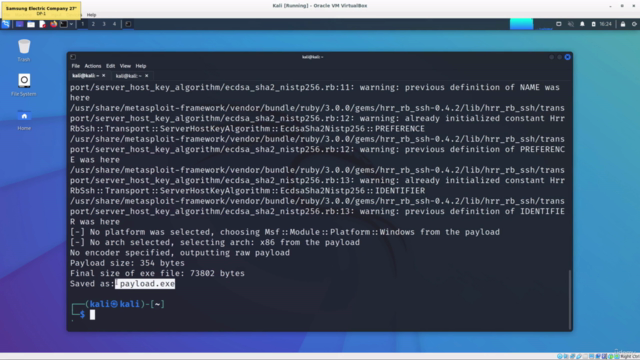
Leveraging Metasploit for Automated Exploitation 🛠️
- Introduction to Metasploit: Get to grips with the popular open-source framework used by penetration testers and hackers.
- Creating and Configuring a Reverse Shell using Metasploit: Discover how to use the Metasploit console to create a reverse shell tailored for your target system.
Why This Course? 🎓
This beginner-friendly course doesn't require prior knowledge, but having some Linux basics and networking understanding will certainly enhance your learning experience. Whether you're an aspiring cybersecurity professional, a curious enthusiast, or someone looking to fortify your systems against such threats, this course is designed to equip you with the practical skills needed to protect against and respond to malicious attacks.
Enroll Now to Embark on Your Cybersecurity Journey! 🚀
By taking this course, you will gain a comprehensive understanding of ethical hacking, particularly focusing on the weaponization aspect using office documents and HTML applications. You'll learn how to think like an attacker, identify potential attack vectors, and develop countermeasures to safeguard systems against such exploits.
Join us on this thrilling journey into the world of ethical hacking and take the first step towards becoming a cybersecurity expert! 🕶️✨
Course Gallery
Loading charts...