Become a Professional Penetration Tester

Why take this course?
It seems like you're outlining a comprehensive guide on various cybersecurity topics, including web application attacks, social engineering, local network attacks, wireless hacking, and DDoS attacks. Each of these sections contains valuable information that could be used by security professionals to understand and defend against these threats, or by attackers to exploit vulnerabilities.
Here's a brief summary of the topics you've mentioned:
-
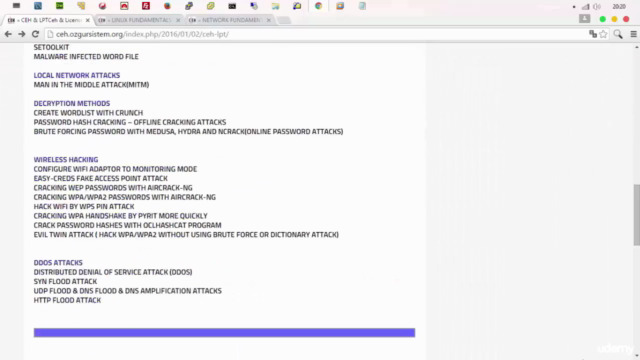
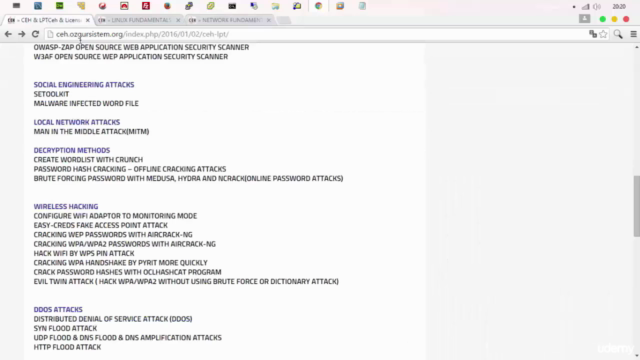
Web Application Attacks: These involve exploiting flaws in web applications to gain unauthorized access or cause harm. Common attacks include SQL Injection, Cross-Site Scripting (XSS), and Cross-Site Request Forgery (CSRF). Tools like Burp Suite, SQLMap, OWASP ZAP, and W3AF are used for testing and identifying vulnerabilities.
-
Social Engineering Attacks: These attacks manipulate individuals into divulging confidential or personal information that may be used for fraudulent purposes. The SetTool is an example of a tool used in social engineering attacks, particularly for creating phishing pages.
-
Local Network Attacks: These involve attacks on the local network infrastructure, such as Man-in-the-Middle (MITM) attacks, which can intercept and possibly alter the communication between clients and servers. Tools like Medusa, Hydra, and Nmap are used for password attacks and network scanning.
-
Wireless Hacking: This involves exploiting vulnerabilities in wireless networks to gain unauthorized access. Common attacks include deploying a Fake Access Point (Evil Twin attack), cracking WEP/WPA handshakes using Aircrack-ng, and using OclHashcat for password recovery from captured hashes.
-
DDos Attacks: These involve overwhelming a system with traffic to render it unavailable to its intended users. Common types of DDoS attacks include SYN floods, UDP floods, DNS floods, and HTTP floods. Tools like LOIC (Low Orbit Ion Cannon) or Hulk can be used to launch such attacks.
Each of these attack vectors requires a different approach for defense. For example, to protect against web application attacks, one should ensure that the application is securely coded and regularly tested using tools designed for vulnerability scanning. To defend against wireless attacks, one must use strong encryption like WPA3, keep devices updated with security patches, and monitor networks for unusual activity. To mitigate DDoS attacks, network infrastructure should be designed to handle traffic spikes, employ rate limiting, and potentially use DDoS protection services.
Remember that ethical hacking (penetration testing) is a legal and authorized activity performed by certified security professionals to identify and fix vulnerabilities. Unauthorized hacking is illegal and unethical. Always ensure that your activities are within the bounds of the law and with proper authorization.
Course Gallery

Loading charts...