Ethical Hacking, Penetration Testing: Buffer Overflow
step by step Learn how to debug & exploit Buffer Overflows and get a shell access on a system
4.08 (49 reviews)

3 587
students
1 hour
content
Jul 2023
last update
$22.99
regular price
Why take this course?
Course Title: Ethical Hacking, Penetration Testing: Buffer Overflow 🛡️✨
Headline: Step by Step Mastery: Debug & Exploit Buffer Overflows for Shell Access 🚀
Course Description:
Welcome to our Ethical Hacking, Penetration Testing: Buffer Overflow course! 🎓
Why Take This Course?
- Understand the system fundamentals and the intricacies of memory management.
- Delve into the world of debugging to explore how CPU registers interact with memory.
- Uncover the mechanics behind buffer overflow vulnerabilities and their implications for security.
- Gain a deep understanding of how hackers think and exploit these vulnerabilities to gain unauthorized access or cause system failures.
Course Highlights:
- Foundational Knowledge: We'll start with the basics, ensuring that no prior training is required. This course is open to all levels, from beginners to seasoned professionals looking to fill gaps in their knowledge.
- Hands-On Learning: Through practical exercises and real-world scenarios, you'll learn how to detect, debug, and exploit buffer overflow vulnerabilities.
- Comprehensive Coverage: From identifying potential targets to writing and executing a reliable exploit, we've got you covered from start to finish.
- Security Best Practices: Learn about the latest preventive measures against buffer overflow attacks and understand the importance of staying ahead in the ever-evolving cybersecurity landscape.
What You Will Learn:
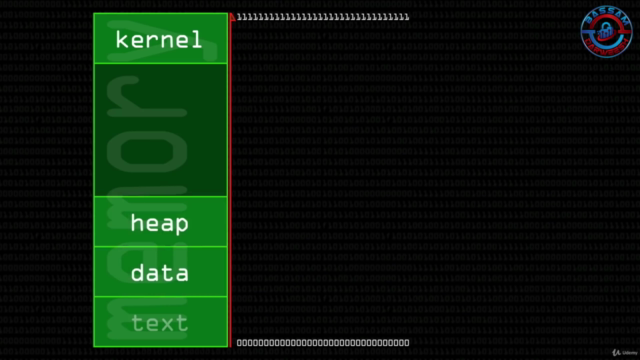
- The architecture and functioning of computer systems, with a special focus on how stack and heap memory spaces operate.
- Techniques to identify buffer overflow vulnerabilities within applications and systems.
- How to write and execute exploit code that leverages these vulnerabilities.
- Strategies to defend against such attacks by understanding the attack vectors and applying appropriate security measures.
Course Benefits:
- Enhanced Skill Set: Elevate your ethical hacking and penetration testing skills, which are highly sought after in the cybersecurity domain.
- Industry Relevance: Learn techniques that are still widely used in the wild, making this knowledge immediately applicable to real-world scenarios.
- Career Advancement: Perfect for those looking to break into or advance within the field of information security and ethical hacking.
- Community Support: Enjoy 24/7 support from our dedicated team. Got a question? Our Q&A section and direct messaging are just a click away!
Course Breakdown:
- Understanding Buffer Overflows: We'll explore what buffer overflows are, how they occur, and why they are a security concern.
- Buffer Overflow Exploits: Learn the process of exploiting these vulnerabilities to gain unauthorized access to a system (also known as "getting a shell").
- Debugging Techniques: Master the art of debugging to understand the state of a program during execution, which is essential for crafting exploits.
- Prevention and Mitigation: Discover best practices for preventing buffer overflows and other security threats.
- Real-World Applications: Apply your new skills in simulated environments that mimic real-world scenarios to ensure you are fully prepared.
Join us on this journey to become a proficient Ethical Hacker and Penetration Tester! Let's conquer the intricate world of buffer overflows together and make a positive impact on the cybersecurity landscape. 🛡️💻
Enroll now and embark on a transformative learning adventure with Ethical Hacking, Penetration Testing: Buffer Overflow course! 🚀✨
Course Gallery



Loading charts...
2563604
udemy ID
17/09/2019
course created date
20/09/2019
course indexed date
Bot
course submited by