Ethical Hacking of RESTful and GraphQL APIs Training Course

Why take this course?
🎓 Ethical Hacking of RESTful and GraphQL APIs Training Course: Become a Successful API Penetration Tester and Bug Bounty Hunter!
Course Introduction (Martin Voelk, Your Seasoned Cyber Security Guide)
Welcome to the Ethical Hacking of RESTful and GraphQL APIs Training Course! 🛡️✨ This course is your gateway into the world of API Penetration Testing and Bug Bounty Hunting. With over 25 years of experience, Martin Voelk, a Cyber Security veteran and holder of prestigious certifications such as CISSP, OSCP, OSWP, Portswigger BSCP, CCIE, PCI ISA, and PCIP, will be your instructor. He has a track record of discovering thousands of critical and high vulnerabilities in various environments.
What You'll Learn
This course is meticulously designed to provide both theoretical knowledge and practical experience with API vulnerabilities. It will take you through a series of labs, some using the Portswigger Web Academy Labs, and others on standalone VMs like crAPI and DVGA. These platforms are freely available for installation on virtualization software like VirtualBox. 🛫
Course Topics at a Glance
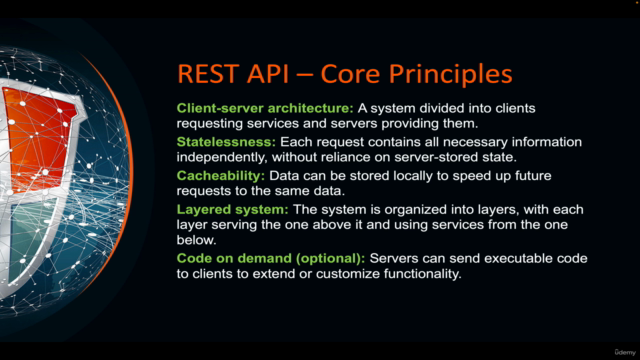
REST API Vulnerabilities
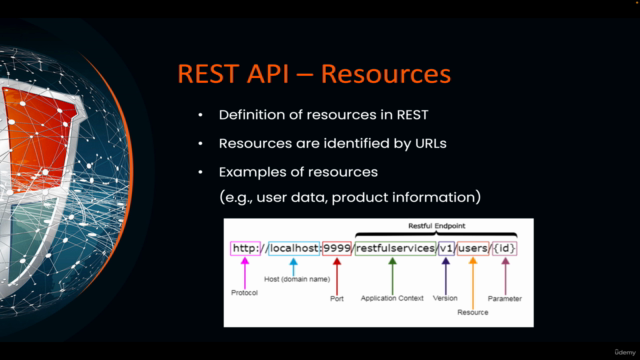
- REST API Introduction
- REST API Discovery and Recon
- REST API Enumeration
- Broken Object Level Authorization (BOLA)
- Broken Authentication
- Broken Object Property Level Authorization
- Excessive Data Exposure
- Mass Assignment
- Unrestricted Resource Consumption
- Broken Function Level Authorization (BLFA)
- Unsafe Consumption of APIs
- Server-side parameter pollution
REST API Security Best Practices
- REST API Security Misconfiguration
- Improper Inventory Management
- Unsafe Consumption of APIs
- Server-side parameter pollution
GraphQL Vulnerabilities
- GraphQL Introduction
- Key terminologies and concepts
- Burp extensions for GraphQL
- Wordlists and Payloads for GraphQL
- Tools and resources for GraphQL
- Batch Query Attacks / Resource Intensive Query Attacks
- Field Duplication Attacks
- Alias based attacks (DoS scenario)
- Directive Overloading
- Object Limit Overriding
- Authentication and Authorization attacks
- Login functions
- Access control issues and IDORs
- Injection attacks (OS Command, SQL, HTML, XSS)
- Request Forgery and Hijacking (RFI, CSRF, CSWH)
- SSRF (Server-side request forgery)
Course Structure
The course is structured to build your skills progressively. You'll start with the basics and gradually move to more complex topics. Each module is designed to challenge and enhance your understanding of API vulnerabilities and how to exploit them ethically.
Notes & Disclaimer 🔒
-
Portswigger Labs: These are freely available for anyone who wishes to practice their skills. All you need is a free account with Portswigger.
-
crAPI and DVGA: Both are open-source tools that can be cloned from GitHub. They are free to use for educational purposes.
-
Response Time: Martin Voelk is committed to responding to your questions in a reasonable time frame.
-
Learning Path: Becoming proficient in Web/Mobile Application Penetration Testing and Bug Bounty Hunting is a journey. It requires patience, dedication, and continuous learning. Utilize resources like Google, Hacker One reports, and in-depth research to enhance your skills.
-
Ethical Use: This course material is for educational purposes only. The information provided must be used responsibly and ethically. Only test platforms you have explicit permission to analyze.
Embark on this journey with us, and transform into a skilled ethical hacker who can navigate the complexities of RESTful and GraphQL APIs. Enroll now and take your first step towards mastering API security! 🕵️♂️🚀
Course Gallery

Loading charts...