Ethical Hacking: Man in the Middle Attacks Basic to Advance

Why take this course?
🌍 Ethical Hacking: Man in the Middle Attacks - Basic to Advanced 🚀
Headline: Unlock the Secrets to Defending Against Man in the Middle (MitM) Attacks with Our Comprehensive Course!
🔐 Course Instructor: Arsalan Saleem
Welcome to a journey through the digital battlefield where understanding the art of deception in cybersecurity is paramount. As a seasoned ethical hacker, Arsalan Saleem will guide you through the labyrinth of Man in the Middle (MitM) attacks, ensuring you emerge with practical and cutting-edge techniques to not only comprehend these threats but also secure your clients and networks against them.
Course Overview:
In the ever-evolving landscape of cybersecurity, knowledge is power. The most applicable approach to safeguard yourself is to stay informed about new threats and the tactics to avoid them. This course will delve into one of the most critical types of attacks: Man in the Middle (MitM) attacks.
What You'll Learn:
-
Fundamentals of MitM Attacks: Understand the concept, implications, and why they are so difficult to prevent. 🎓
-
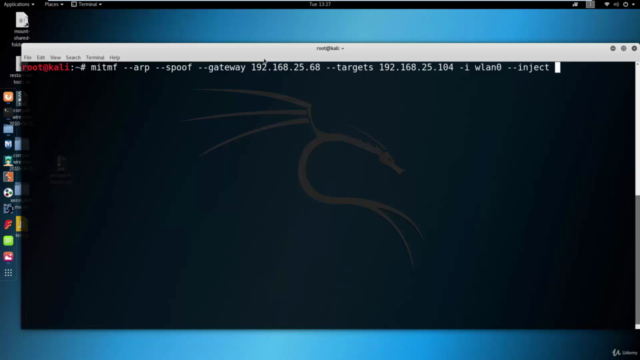
Different Types of MitM Attacks: Explore the various categories including Arp Poisoning, Session Hijacking, DNS Spoofing, and Fake Access Points through engaging practical demonstrations and hands-on training. 🖥️
-
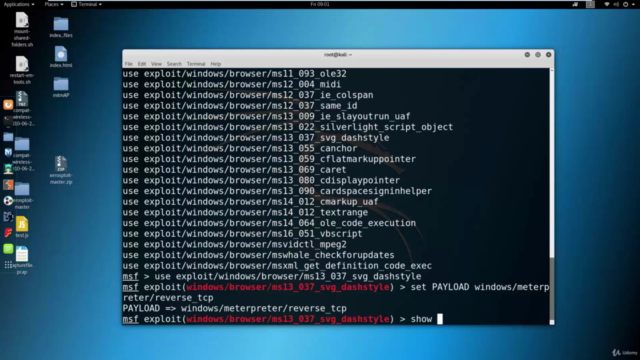
Advanced MitM Techniques: Gain insights into more sophisticated attacks where you'll capture screenshots of a victim's machine and eventually aim to gain full access, all within an ethical framework. 🛡️
-
Prevention Strategies: Learn how to fortify your networks against these elusive threats with effective countermeasures. 🛡️
Course Structure:
-
Introduction to Man in the Middle Attacks:
- What is a MitM attack?
- The importance of understanding these attacks.
-
Types of MitM Attacks:
- Arp Poisoning: Routing attacks where the attacker interferes with the ARP process.
- Session Hijacking: Taking over a user's session to gain unauthorized access.
- DNS Spoofing: Redirecting users to malicious sites by corrupting DNS data.
- Fake Access Points (Evil Twin Attacks): Setting up a rogue Wi-Fi network to trap users.
-
Practical Demonstrations and Hands-On Training:
- Step-by-step guidance on setting up labs for practical exercises.
- Real-world examples and demonstrations of each attack type.
-
Advanced MitM Attacks:
- Capturing sensitive data and screenshots.
- Exploiting vulnerabilities to gain complete access to a victim's machine.
-
Preventing MitM Attacks:
- Understanding the defensive techniques to secure your network.
- Implementing best practices for network security.
Why Take This Course?
-
Practical Knowledge: Gain hands-on experience with real-world scenarios, ensuring you understand how to both execute and prevent MitM attacks. 🔬
-
Expert Instruction: Learn from an ethical hacker with extensive experience in the field. 🎓
-
Comprehensive Coverage: From basic understanding to advanced techniques, this course covers it all. ✅
-
Stay Ahead of the Curve: In cybersecurity, knowledge becomes obsolete quickly. Stay ahead by learning the latest tactics and tools used by professionals in the field. 🚀
Join us on this course to master the art of defending against Man in the Middle attacks. Whether you're an IT professional, a cybersecurity enthusiast, or looking to advance your skills in ethical hacking, this course will equip you with the knowledge you need to navigate the complex world of cyber threats confidently. 🛡️💻✨
Enroll now and secure your digital realm! #EthicalHacking #Cybersecurity #ManInTheMiddle #CyberDefense #OnlineLearning
Course Gallery

Loading charts...