Computer Security: A Hands-on Approach
Why take this course?
🎉 Master Computer Security with Expertise and Interactive Labs! 🚀
Course Title: Computer Security: A Hands-On Approach
Instructor: Wenliang Du
Course Headline: Attacks and Defense: Unveiling the Inner Workings of Buffer Overflow, Race Condition, Dirty COW, Meltdown & Spectre, Shellshock, Format String Vulnerabilities
Dive Deep into Cybersecurity with Real-World Application!
Welcome to "Computer Security: A Hands-On Approach," where you'll embark on an in-depth journey through the landscape of computer security. This isn't just a theoretical course; it's a practical bootcamp designed for those eager to understand and combat some of the most pervasive and sophisticated attacks targeting modern systems.
Why Take This Course?
- Cutting-Edge Content: Learn about both classical and contemporary security threats, including the infamous Meltdown and Spectre vulnerabilities that have affected a significant portion of the world's computing hardware.
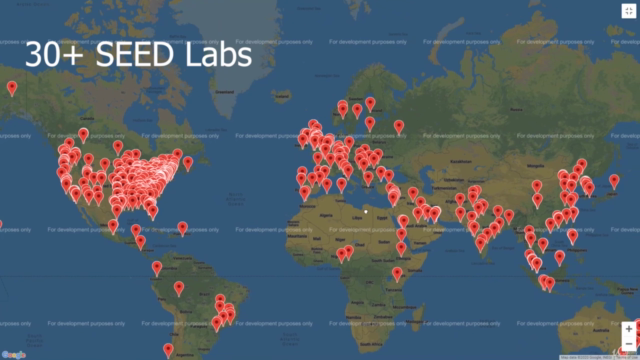
- Hands-On Experience: Engage with SEED labs, which provide an interactive, real-world environment to practice your skills safely and effectively. Over 1000 institutions worldwide use these labs for their students!
- Expert Guidance: Follow along with the course textbook, "Computer & Internet Security: A Hands-On Approach, 2nd Edition," co-authored by the instructor himself, which has been adopted by over 120 universities and colleges globally.
Course Highlights:
- Buffer Overflow Attacks: Understand how attackers exploit buffer overflows to execute arbitrary code on victim systems.
- Race Condition Vulnerabilities: Learn how to recognize and mitigate race conditions that can lead to critical security breaches.
- Dirty COW (Copy-On-Write) Exploitation: Gain insights into the Dirty COW vulnerability and its implications on Linux systems.
- Meltdown & Spectre Exploitation: Delve into the complexities of these hardware-level attacks and how to defend against them.
- Shellshock (Bash Bug) Exploitation: Discover the dangers of unprotected environment variables, like those found in Bash.
- Format String Vulnerabilities: Learn how attackers can manipulate applications to perform unauthorized operations using format strings.
What You Will Achieve:
- Practical Skills: Develop a deep understanding of the inner workings and countermeasures for various security threats.
- Professional Knowledge: Gain the expertise needed to protect systems from attackers, whether you're a developer, system administrator, or cybersecurity enthusiast.
- Confidence in Your Skills: By using SEED labs, you will confidently apply your knowledge to real-world scenarios, ensuring you are prepared to tackle security challenges head-on.
Join the Global Community of Cybersecurity Professionals!
Whether you're looking to enhance your current cybersecurity skill set or aspire to become a cybersecurity expert, this course offers a comprehensive and practical approach to learning. Don't just learn about computer security—experience it through hands-on exercises and come out on top in the battle against malicious attacks.
🎓 Enroll Now and Transform Your Cybersecurity Career! 💻
Start Learning Today - Elevate your understanding of computer security with this unparalleled, hands-on learning experience!
Course Gallery



Loading charts...