Cybersecurity & Kali Linux by TechLatest - Part 3 of 6

Why take this course?
🔒 Course Title: Cybersecurity & Kali Linux by TechLatest - Part 3 of 6
📚 Course Description:
Note: This is part 3 of 6 on Cybersecurity & Kali Linux. Please enroll to all other 5 parts for the complete course experience.
Unlock the secrets of cybersecurity, penetration testing, ethical hacking, and digital defense with our comprehensive and practical TechLatest Cybersecurity & Kali Linux course. This program is designed to provide both the theoretical knowledge and hands-on skills necessary to excel in the ever-evolving field of cybersecurity.
What You'll Learn:
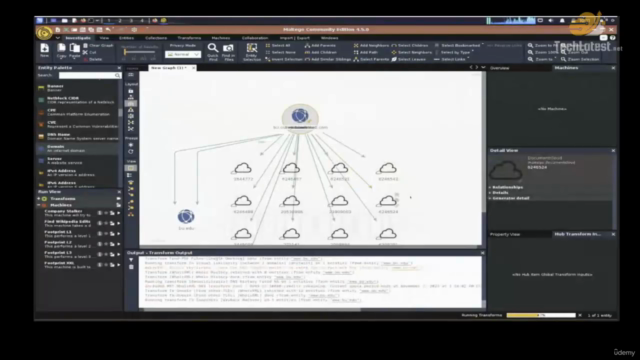
- Essential Reconnaissance Techniques: Gain a deep understanding of Open Source Intelligence (OSINT) gathering, reconnaissance, target validation, and subdomain discovery.
- Kali Linux Mastery: Explore the full potential of Kali Linux tools in a structured, ethical learning environment.
- Practical Skills: Experiment with OS fingerprinting, exploitation, password cracking, web application testing, wireless network assessments, and social engineering techniques.
- Ethical Hacking Tools: Learn how to use an array of Kali Linux tools effectively and responsibly.
- Real-World Scenarios: Apply your knowledge in realistic cybersecurity scenarios that mimic real-world challenges.
Course Structure:
- Understanding Cybersecurity Fundamentals: Get to grips with the foundational concepts of cybersecurity.
- OSINT & Target Validation: Master the art of gathering intelligence and validating targets within legal boundaries.
- Kali Linux Tools for OS Fingerprinting: Learn how to identify and fingerprint different operating systems.
- Subdomain Discovery Techniques: Uncover hidden elements of a target's infrastructure with advanced subdomain discovery methods.
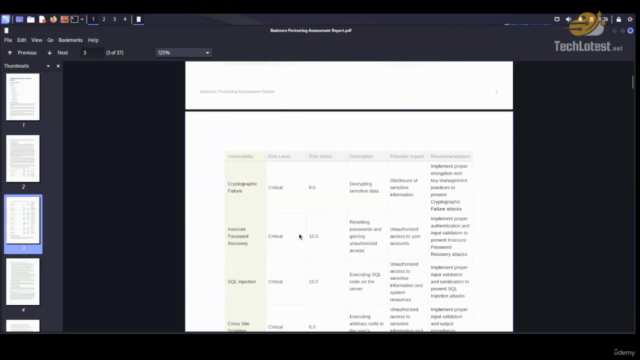
- Exploitation Basics: Dive into the basics of exploitation, understanding how vulnerabilities can be leveraged.
- Password Cracking Techniques: Discover methods to crack passwords and understand the importance of strong authentication measures.
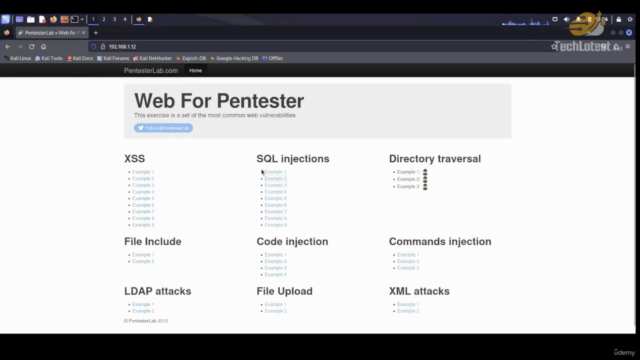
- Web Application Testing: Learn how to test web applications for security vulnerabilities.
- Wireless Network Assessments: Explore the airwaves with wireless network assessments, identifying potential security risks.
- Social Engineering Strategies: Understand the psychological tactics used in social engineering and learn how to protect against such attacks.
By completing this course, you will:
- Possess a solid foundation in cybersecurity concepts.
- Have practical experience with Kali Linux tools and methodologies.
- Feel confident in your ability to secure systems and networks against threats.
- Be equipped with the necessary skills to thrive in the field of cybersecurity.
👩💻 Who is this for? This course is designed for IT professionals, network security engineers, penetration testers, and anyone interested in expanding their knowledge of cybersecurity and ethical hacking using Kali Linux. Whether you're starting your career or looking to enhance your existing skills, this course will provide the guidance and practice you need to excel.
🛠️ Tools & Technologies Covered:
- Kali Linux
- Various Cybersecurity Tools and Frameworks
- Network Scanners
- Vulnerability Scanners
- Password Cracking Tools
- Wireless Assessment Tools
- Social Engineering Techniques
📅 Enroll Now and Stay Ahead in Cybersecurity: Join us on this journey into the world of cybersecurity. With each module, you'll build upon your knowledge and skills, ensuring you have a comprehensive understanding by the end of the course. Enroll in part 3 today and secure your place in the next modules to come!
Course Gallery

Loading charts...