Complete WIFI Hacking Course With Powerful MITM Techniques

Why take this course?
🔐 Unlock the Secrets of WIFI Hacking: A Comprehensive Journey with Maneesha S. Nirmanci
Welcome to the Best WIFI Hacking Course Ever!
With Complete WIFI Hacking Course With Powerful MITM Techniques, you'll embark on an educational adventure that will transform you into a master of network security and wireless penetration testing. 🚀
Course Breakdown
Dive deep into the world of WiFi hacking with Maneesha S. Nirmanci, where you'll learn everything from social engineering to advanced password recovery. Here's what you can expect:
Section 1: Setting Up Your Penetration Lab
- Installing Kali Linux within VMware
- Configuring your system for optimal wireless penetration testing performance
- Selecting and setting up a compatible wireless adapter
Strengthen Your WiFi Penetration Testing Foundation
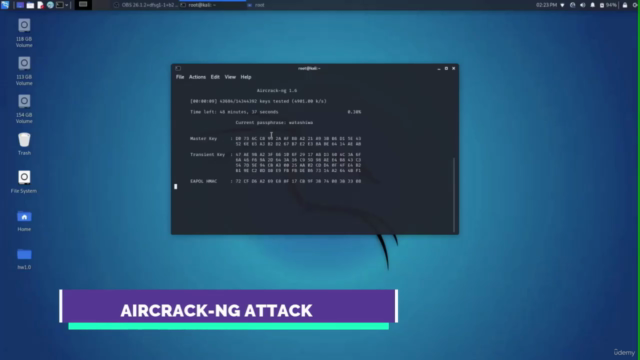
- Get hands-on experience with the Aircrack-ng suite
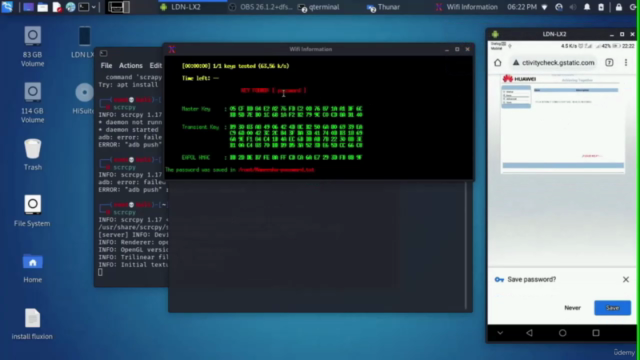
- Master the art of capturing WPA handshakes
- Learn to automate the password recovery process using tools like Wifite
Section 2: Exploring Hashcat for Advanced Password Recovery
Discover four sophisticated password recovery techniques:
- Brute-force attacks
- Dictionary attacks
- Combinator attacks
- Rule-based attacks
Master WiFi Network Hacking with WPA/WPA2 PSK By the end of this section, you'll have a solid grasp on how to crack WiFi networks using powerful techniques.
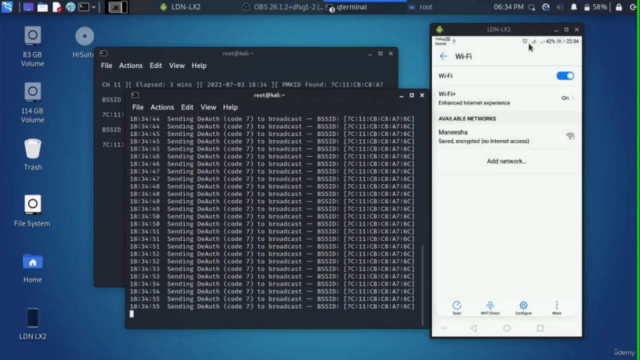
Section 3: Mastering MITM Attacks
- Learn how to set up your tools (airgeddon and fluxion) for two potent MITM attack methods:
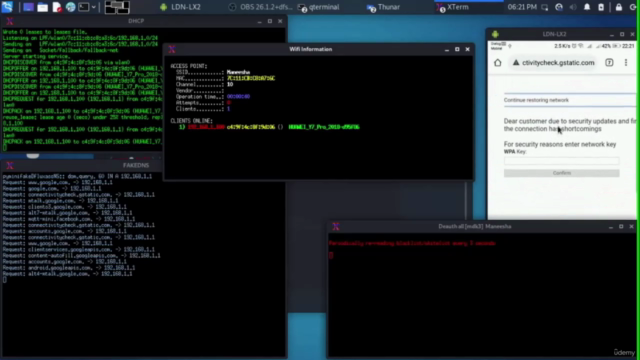
- Evil Twin Attack Using Captive Portral: Create a fake WiFi network that tricks users into entering their credentials.
- Fake Firmware Upgrade Method: Deceive users into upgrading their firmware to your malicious version.
Build Your Own Evil-Twin AP Get hands-on experience in creating a custom Evil-Twin Access Point using Hostapd, Dnsmasq, and Openssl. Learn how to integrate these components into Airgeddon for an automated setup.
Continuous Course Updates
Maneesha is committed to keeping this course up-to-date with the latest techniques and tools. You'll receive value for your investment as new content is added regularly. 📚✨
Final Section: Advanced MITM Techniques
Master two exclusive MITM attack methods covered in this course. You'll learn how to:
- Redirect users to a fake login page
- Perform powerful attacks using the tools provided
Disclaimer
🚫 Important Note All techniques taught in this course are intended for educational and ethical purposes only. The content is not meant to promote any illegal activities. It is your responsibility to ensure compliance with all relevant laws and regulations regarding computer security and WiFi hacking in your jurisdiction before attempting to use the materials or information contained within this course. Maneesha Nirmanci takes no responsibility for any misuse of these techniques.
Let's Start Learning! 🎓
Embark on your journey to master WiFi hacking with Complete WIFI Hacking Course With Powerful MITM Techniques. Equip yourself with the knowledge and skills to navigate the complex landscape of network security. Your adventure into the world of cybersecurity begins now!
Course Gallery
Loading charts...
Comidoc Review
Our Verdict
This 2-hour Complete WIFI Hacking Course has garnered an impressive rating of 4.46/5 from over 20000 subscribers since its release in July 2021 and last update in March 2023, making it a worthwhile contender in your hunt for ethical hacking expertise. Glean essential WiFi security insights through its detailed penetration testing lab setup guide while engaging with Hashcat's password recovery techniques as well as other rainbow table attacks. Despite minor presentation and outdated content issues along with occasional code complications, this Udemy course excels in clarifying complex hacking ideas, enabling beginners to swiftly grasp fundamental WiFi hacking principles.
What We Liked
- Comprehensive coverage of WiFi hacking techniques, including WPA/WPA2 PSK password cracking and MITM methods
- Detailed walkthrough in setting up a wireless penetration testing lab, with custom templates integration
- Instructor's clear explanations that cater to beginners, facilitating quick understanding of WiFi hacking concepts
- Valuable insights on advanced password recovery using Hashcat and rainbow table attack
Potential Drawbacks
- A few instances of outdated content, such as mentioning only WiFi 4 capable adapters
- Some users mentioned a need for clearer instructions when exporting captured credentials to an external computer or email
- Concerns over incomplete coverage of some methods and minor code issues in Evil Twin attack DummyWeb page
- Occasional presentational concerns, such as focusing on the instructor's process instead of theoretical background