Complete Guide to Ethical Hacking

Why take this course?
🛡️ Complete Guide to Ethical Hacking: Exam Prep Course 🚀
Unlock the Secrets of Cybersecurity with Our Complete Guide to Ethical Hacking! 🌐✨
Are you ready to dive into the world of network security and ethical hacking? Our Complete Guide to Ethical Hacking course is meticulously crafted to provide you with an exhaustive understanding of the subject matter, along with hands-on experience that will equip you with the skills needed to excel in this high-demand field.
Course Overview:
📚 Who should take this course? This course is a must for cybersecurity enthusiasts, IT professionals, network administrators, penetration testers, security officers, law enforcement personnel, and anyone aspiring to become an ethical hacker. It's the perfect step if you're aiming to attain the Certified Ethical Hacker (CEH) certification.
Course Highlights:
-
In-Depth Knowledge: Gain comprehensive insights into the principles, tools, and techniques used by ethical hackers to fortify network systems against threats.
-
Practical Skills: Learn by doing with real-world scenarios that test your abilities in identifying vulnerabilities, exploiting weaknesses, and protecting against malicious attacks.
-
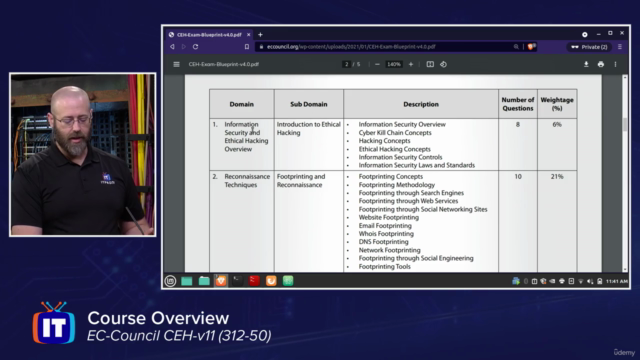
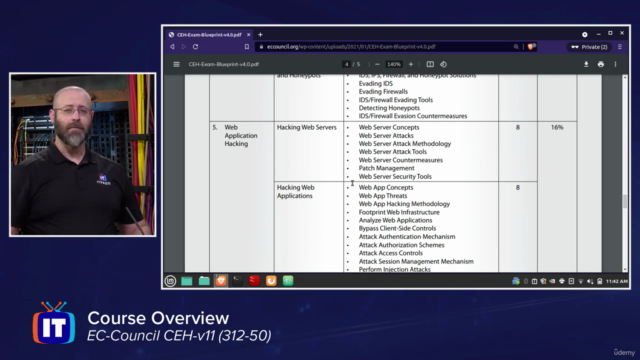
Exam Preparation: This course is meticulously aligned with the CEH v11 exam objectives to ensure you're thoroughly prepared for the certification exam.
Key Topics Covered:
🔥 Understanding Ethical Hacking:
- Learn the foundational concepts of ethical hacking and how it serves as a proactive defense strategy in cybersecurity.
🔒 Identifying Network Vulnerabilities:
- Master the art of detecting security weaknesses within network systems, and understand the importance of addressing these issues promptly.
💥 Exploiting Network Systems:
- Get hands-on experience with exploitation techniques to understand how vulnerabilities can be leveraged by attackers.
🪠 Malware Analysis:
- Dive into the world of malware, learning about its various forms and how to counteract their impact on networks and systems.
📊 Network Traffic Analysis:
- Analyze network traffic patterns to detect anomalies that could indicate security breaches or suspicious activities.
👥 Social Engineering Tactics:
- Learn to recognize and defend against social engineering attacks, which often serve as the gateway for cyber attacks.
🛫 Web Application Penetration Testing:
- Explore common web application vulnerabilities and learn how to exploit them, ensuring that applications are secure from top to bottom.
📡 Wireless Network Hacking:
- Discover the security challenges specific to wireless networks and how to mitigate potential risks.
⫫ Cryptography Fundamentals:
- Understand the role of cryptography in protecting data and communication, and learn about various encryption methods.
🌠 Cloud Security Risks:
- Navigate the complexities of cloud computing environments, recognizing common security risks and how to address them.
Why Choose This Course?
- Foundational Knowledge: It is highly advisable to complete relevant foundational courses such as CompTIA Network+, Security+, or EC-Council's Certified Security Specialist (ECSS) before starting this course. These will provide you with the essential knowledge and skills for a successful learning journey.
Who Should Enroll?
This course is designed for cybersecurity professionals, IT managers, network administrators, penetration testers, security officers, law enforcement personnel, and anyone else committed to mastering ethical hacking and enhancing network security measures.
Important Note:
- Stone River eLearning is an independent platform and is not affiliated with EC-Council. The course content aligns with the CEH v11 exam objectives, but please be aware that completing this course does not guarantee certification from EC-Council. You must register for and pass the official CEH v11 exam through EC-Council to earn your Certified Ethical Hacker certification.
Embark on your journey to become a skilled ethical hacker today with our comprehensive guide! 🔐💻🚀
Course Gallery


Loading charts...