Building A Professional Ransomware Attack Using Java

Why take this course?
🎉 Building a Professional Ransomware Attack Using Java 🕷️
Course Headline:
Dive into the world of ethical hacking with our comprehensive course, where you'll learn to construct a sophisticated ransomware virus using the Java programming language. Gain invaluable knowledge and skills in cryptography, email automation, and user interface design, all within an ethical framework. 🔒✨
Course Description:
Welcome to Building A Professional Ransomware Attack Using Java, an advanced course designed for those with a passion for cybersecurity and ethical hacking. In this course, we will embark on a journey from the theoretical underpinnings of cryptography to the practical implementation of a ransomware attack using Java. Our goal is to understand the intricacies of creating such a program without causing any real harm or engaging in illegal activities.
Key Course Takeaways:
- Cryptography Basics: Understand the fundamental concepts of cryptography, which are essential for any secure encryption method.
- Algorithm Development: Propose and develop an algorithm tailored to encrypt your target's data effectively.
- Java Programming: Write professional Java code step by step, focusing on readability and best practices.
- Email Automation: Learn to send emails from within the program to inform you of important details about the attack's success.
- Graphical User Interface (GUI): Construct a user interface frame using Java, enhancing user interaction with your program.
🔐 Building a Malicious Code (Ransomware):
Develop a ransomware program that operates solely on the system where it is executed. You will learn how to embed this program within .exe and .SFX files, making it undetectable and non-suspicious for the target user. 🛡️
Email Alert Features:
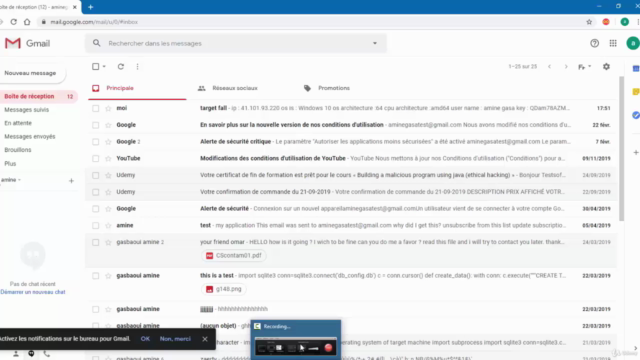
After the ransomware is initiated by the target, the program will automatically send an email to your specified address containing:
- The target's IP address.
- Information about the operating system and CPU architecture used by the target.
- The target's administrator username.
- The key required for decrypting the data. 📧
Programming Functions to Build:
- Encryption Algorithm: A function that takes a text input and returns an encrypted byte array.
- Random File Name Generation: Create a random file name to store the encrypted data.
- Important Data Generator: Develop a function that generates a file containing important decryption information and contact details for the attacker.
- File Encryption: A robust function capable of reading and encrypting all types of files (images, text, music, videos).
- String to Byte Converter: Convert text into a byte format for encryption purposes.
- Email Class: Craft an email class that allows you to send notifications to your specified address with critical data from the target system.
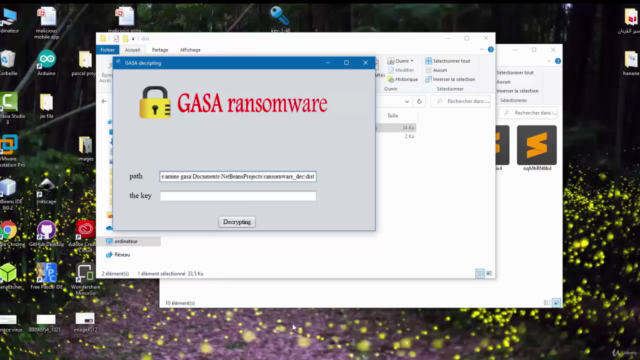
Decryption Application:
Alongside the ransomware, we will also build a desktop decryption application to restore the target's data. This will involve coordinating different components and objects within the Java program to achieve our ethical objectives. 🗝️
This course is perfect for those with a solid foundation in programming and coding. It requires patience, dedication, and an eagerness to explore complex projects like these. By the end of this course, you'll not only understand how ransomware functions but also be equipped with the skills to create one, ethically and for educational purposes only. 🎓
Join us on this thrilling journey into the world of cybersecurity and ethical hacking with Java! Let's unlock the secrets of building a professional ransomware attack responsibly and securely.
Course Gallery
Loading charts...