Be A White Hat Hacker and Pen Tester

Why take this course?
🧙♂️ Transform Your Skills with "Be A White Hat Hacker and Pen Tester" 🚀
Course Title: Be A White Hat Hacker and Pen Tester
Course Headline: Master Ethical Hacking Concepts & Practical White Hat Hacking Techniques and Pen Testing!
Dive into the World of Cybersecurity with Our Comprehensive Online Course!
Welcome to the realm where curiosity meets skill, and your passion for cybersecurity transforms into expertise. This isn't just another course on ethical hacking; it's a journey into the practical world of penetration testing (Pen Testing). With Eduonix Learning Solutions, you will learn how to think like a hacker without crossing ethical boundaries.
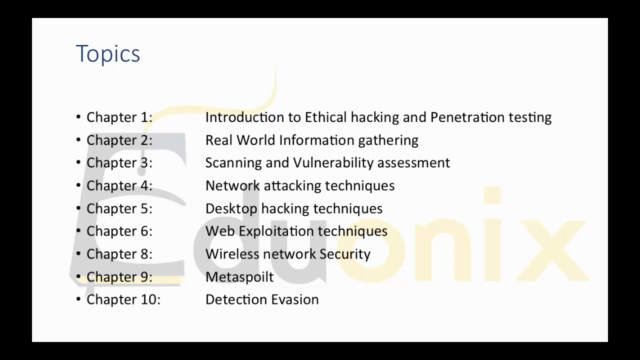
Course Overview 🔍
The course is meticulously structured into key sections, each designed to build upon the previous, ensuring a robust understanding of white hat hacking and penetration testing. From foundational concepts to advanced techniques, you will navigate through this course with ease.
Ethical Hacking Concepts 🛡️
- What is Ethical Hacking? Discover the essence of ethical hacking and the different types of hackers. Explore hacktivism, understand its significance, and get introduced to practical pen testing techniques.
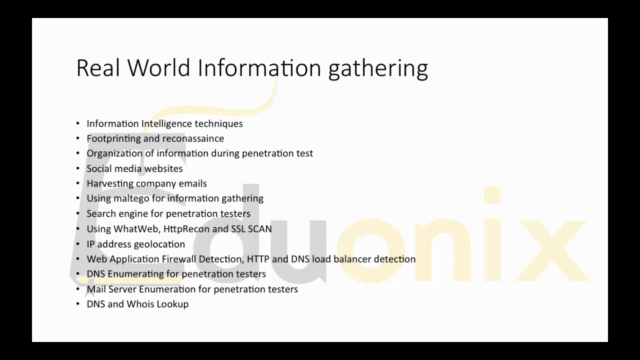
Real World Information Gathering 🕵️♂️
- Foot Printing & Reconnaissance: Learn how to gather information about your target without raising suspicion.
- Email Harvesting: Master the art of finding email addresses associated with your targets.
- SSL Scan, Maltego, Whatweb, HttpRecon: Utilize these tools to glean vital data from your subjects.
- IP Address Geolocation, DNS and Mail Server Enumeration: Understand the ins and outs of network infrastructure mapping.
Scanning and Vulnerability Gathering 🛠️
- Scapy: Craft packets and perform port scans to identify vulnerabilities.
- Network Scanning Techniques: Learn how to systematically assess networks for weaknesses.
- Vulnerability Identification: Pinpoint potential attack vectors in any system.
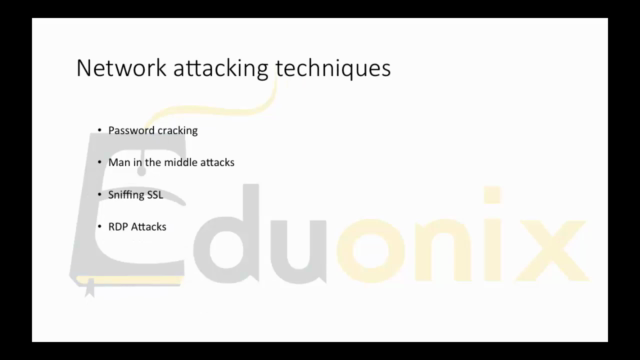
Network Attacking Techniques 🛡️
- Password Cracking: Gain access to systems through weak passwords.
- MITM (Man-in-the-Middle) Attacks: Intercept and possibly alter the communication between two parties without their knowledge.
- Sniffing SSL and RDP Attacks: Capture sensitive information transmitted over networks.
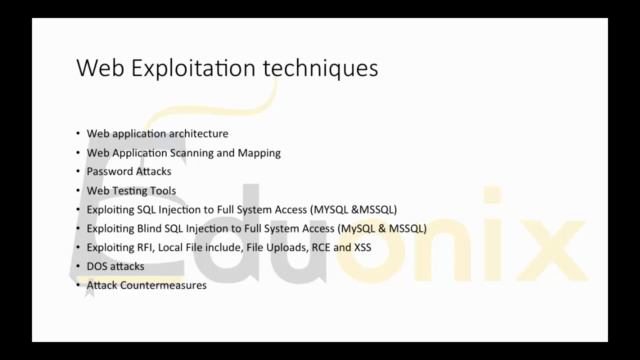
Web Exploitation Techniques 💻
- SQL Injections, RCE (Remote Code Execution), DOS Attacks: Learn how to exploit web vulnerabilities effectively.
Wireless Network Security 📶
- Standards in Wireless Security: Understand the protocols and standards that govern wireless communications.
- WEP Encryption: Crack WEP keys to gain access to wireless networks.
- Wireless Sniffing: Intercept wireless communications to analyze traffic and data.
- Protecting Wireless Networks: Learn how to secure your own network from unauthorized access.
Metasploit 🛡️
- Metaspoilt Tool: Get hands-on experience with Metaspoilt, one of the most widely used frameworks for penetration testing and attack vector exploration.
Detection Evasion 🕵️♂️
- Evading Detection: Discover techniques used to bypass intrusion detection systems and antivirus solutions.
By the end of this course, you won't just be knowledgeable in ethical hacking; you will have the expertise to perform comprehensive penetration tests, identify vulnerabilities, and implement effective countermeasures. 🛡️✨
Embark on your journey to becoming a certified white hat hacker and pen tester today! Let's decode the digital frontier together with Eduonix Learning Solutions.
Course Gallery
Loading charts...