AZ-700 Designing & Implementing Azure Networking with SIMS

Why take this course?
To address the tasks you've outlined, let's break them down and discuss each component. Here's how you can approach the design and implementation of Azure networking services, including load balancing, Application Gateway, Front Door, Traffic Manager, Private Link, service endpoints, network security groups (NSGs), Azure Firewall, and Web Application Firewall (WAF).
Azure Load Balancer
Map requirements to features and capabilities:
- Determine if you need basic or advanced SKU.
- Decide between internal (VNET-to-VNET) and public (internet-facing).
- Understand the different types of load balancing: layer 4 (TCP, UDP), layer 7 (HTTP/S), and WebSocket.
Appropriate use cases:
- Multi-tiered application deployment with high availability and auto-scaling needs.
- Load distribution across multiple VMs or instances.
Choose an Azure Load Balancer SKU and tier:
- Basic SKU for single VM scale sets, internal load balancing, or classic deployment model.
- Standard SKU for more advanced capabilities like SSL termination and advanced health probes.
Choose between public and internal:
- Public for internet-facing applications.
- Internal for VNET to VNET traffic within Azure.
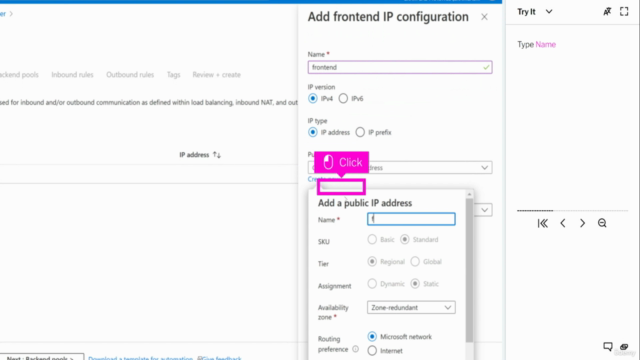
Create and configure an Azure Load Balancer:
- Set up a load balancer in the desired resource group.
- Define backend pools, health probes, load balancing rules, and associated networks.
Implement a load balancing rule:
- Configure the necessary parameters to direct traffic as needed.
Create and configure inbound NAT rules:
- Set up Network Address Translation (NAT) rules for internal VMs to access the internet.
Create and configure explicit outbound rules, including SNAT:
- Define Source Network Address Translation (SNAT) to modify the source IP address of outgoing traffic from your VMs.
Removing the Azure Load Balancer before moving forward:
- Use the Azure portal or ARM templates to delete the load balancer when it's no longer needed.
Azure Application Gateway
Map requirements to features and capabilities:
- Understand WAF capabilities if security is a concern.
- Identify the need for SSL termination, session affinity, and URL rewriting.
Appropriate use cases:
- Application deployments requiring advanced load balancing features like session persistence or URL rewriting.
- Enhanced security with WAF rules.
Starting the setup process for an Azure Application Gateway:
- Create a new application gateway instance in your resource group.
- Define backend pools, routing rules, HTTP settings, and listen to ports.
Configure back-end pools:
- Add VMs or VMSS instances as members of the backend pool.
Configure routing rules:
- Set up paths, conditions, and backend pool associations.
Configure health probes and HTTP settings:
- Define how to test the health of your backend resources.
Configure WAF policies if needed:
- Define detection or prevention mode and create OWASP rules as per your security requirements.
Associate a WAF policy:
- Link the Application Gateway with the configured WAF policy.
Azure Front Door
Map requirements to features and capabilities:
- Global load balancing, caching, persistent connections, and SSL termination at the edge.
Design a WAF deployment:
- Define the deployment strategy considering geographic distribution and latency.
Configure a rule for WAF on Azure Front Door:
- Set up rules within Front Door to protect your global applications.
Azure Traffic Manager
Map requirements to features and capabilities:
- Global traffic routing with DNS-based load balancing.
Appropriate use cases:
- Applications that require globally distributed users to be routed to the nearest or best endpoint.
Azure Private Link
Design a WAF deployment:
- Understand how Private Link enhances security by providing a private endpoint into Azure services and your own resources.
Service endpoints:
- Create service endpoints for Azure services like SQL Database, Storage Accounts, etc., to access them through a private endpoint in your VNET.
Network Security Groups (NSGs)
Design and implement NSGs:
- Define rules to allow or deny traffic to your resources based on IP addresses, ports, and protocols.
Verify and Validate NSG flow logs:
- Use NSG flow logs for monitoring and auditing traffic flows through the network security groups.
Azure Firewall and Azure Firewall Manager
Design an Azure Firewall deployment:
- Set up a firewall instance and define rules to control traffic based on IP address, port, protocol, and domain names.
Create and implement Azure Firewall Manager policies:
- Use Firewall Manager to centrally manage and enforce security policies across multiple subscriptions and resources.
Implement a secure hub by deploying Azure Firewall inside an Azure Virtual WAN hub:
- Centralize your network security by integrating Azure Firewall with Azure Virtual WAN for simplified management and better security.
Removing unneeded Azure resources:
For any of the above services, when you no longer need them, you can delete them through the Azure portal or using ARM templates. This helps in reducing costs and maintaining a clean infrastructure setup.
Remember to always test configurations in a development or staging environment before deploying changes to production. Additionally, ensure that you comply with your organization's security policies and best practices for managing Azure resources.
Course Gallery
Loading charts...